| |
| |
Explain Plurilock Quickly to Fellow Stakeholders with This Simple PDF.
|
|
|
|
|
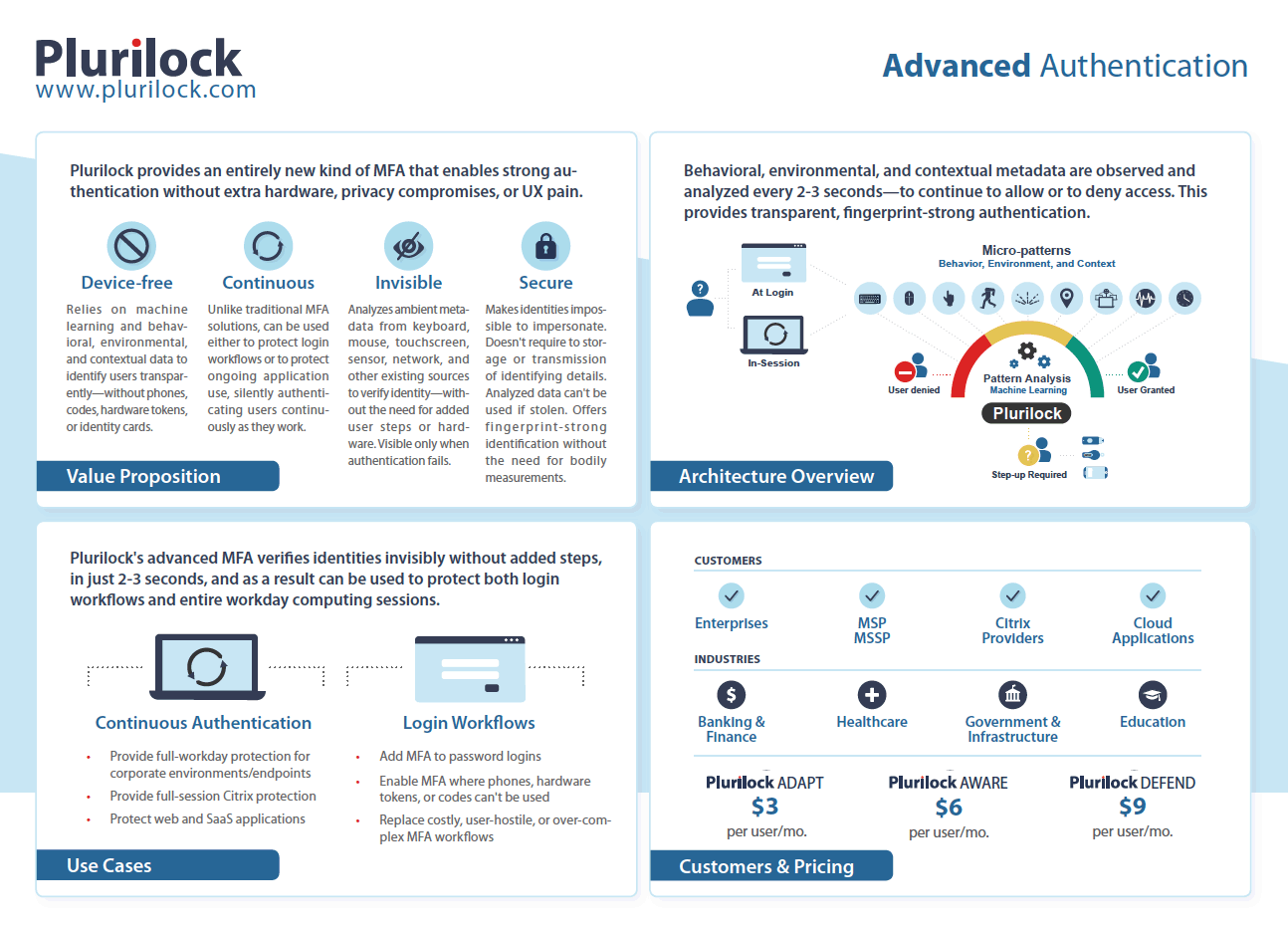
The Plurilock Quad Chart
Plurilock’s value proposition, use cases, basic architecture, and typical clients and pricing—all in a single page. Shareable and presentable.
|
| To make the right MFA choices, it’s important to understand your objectives—and how MFA technologies line up with them.
|
|
| |
You Need Advanced Authentication for These Seven Good Reasons
If any of these sound like you, it’s time to move beyond legacy MFA solutions—and their risks and limitations.
Read the article →
|
| |
Know Which MFA Technologies to Avoid—and Which to Embrace
What is MFA meant to provide, and which MFA methods actually deliver it? Summaries and ratings for each technology.
Read the article →
|
|

|
Healthcare organization? Need EMR or EHR protection? Plurilock can help you to meet or exceed HIPAA—without driving providers crazy.
See the details →
|
|
|

|
Get authentication right. Struggling with details, options, and policies? Our 2019 authentication guide has the data you need to clear the fog.
Get the guide →
|
|
|

|
Password and resource sharing. Audit nightmares. Why continuous authentication may be the MFA technology you actually need.
Read the article →
|
|
|
|
Need more hard data and details about Plurilock?
Browse through our list of PDF resources about Plurilock products and cybersecurity best practices.
|
|
|
Plurilock, Inc.
c/o CTA
335 Madison Avenue, 4th Floor
New York, NY 10017
|
|
|
Plurilock values the privacy and security of its customers. We encourage you to review our privacy policy.
Copyright © 2019 Plurilock Security Solutions, Inc. All rights reserved.
MESSAGE: TEMPLATE
|
|
|