Least privilege access, CASB, and DLP meet AI identity confirmation.

The Need
True least privilege and zero trust require true real-time identity.
Granting only the access needed, only those who need it, and only when and for as long as it is needed...is difficult in the real world.
The stickiest of all problems is user identity—the “who” of computing. All the complex security policies in the world won't safeguard your data if the session is stolen but the key is still valid.
Enter Plurilock AI Complete.
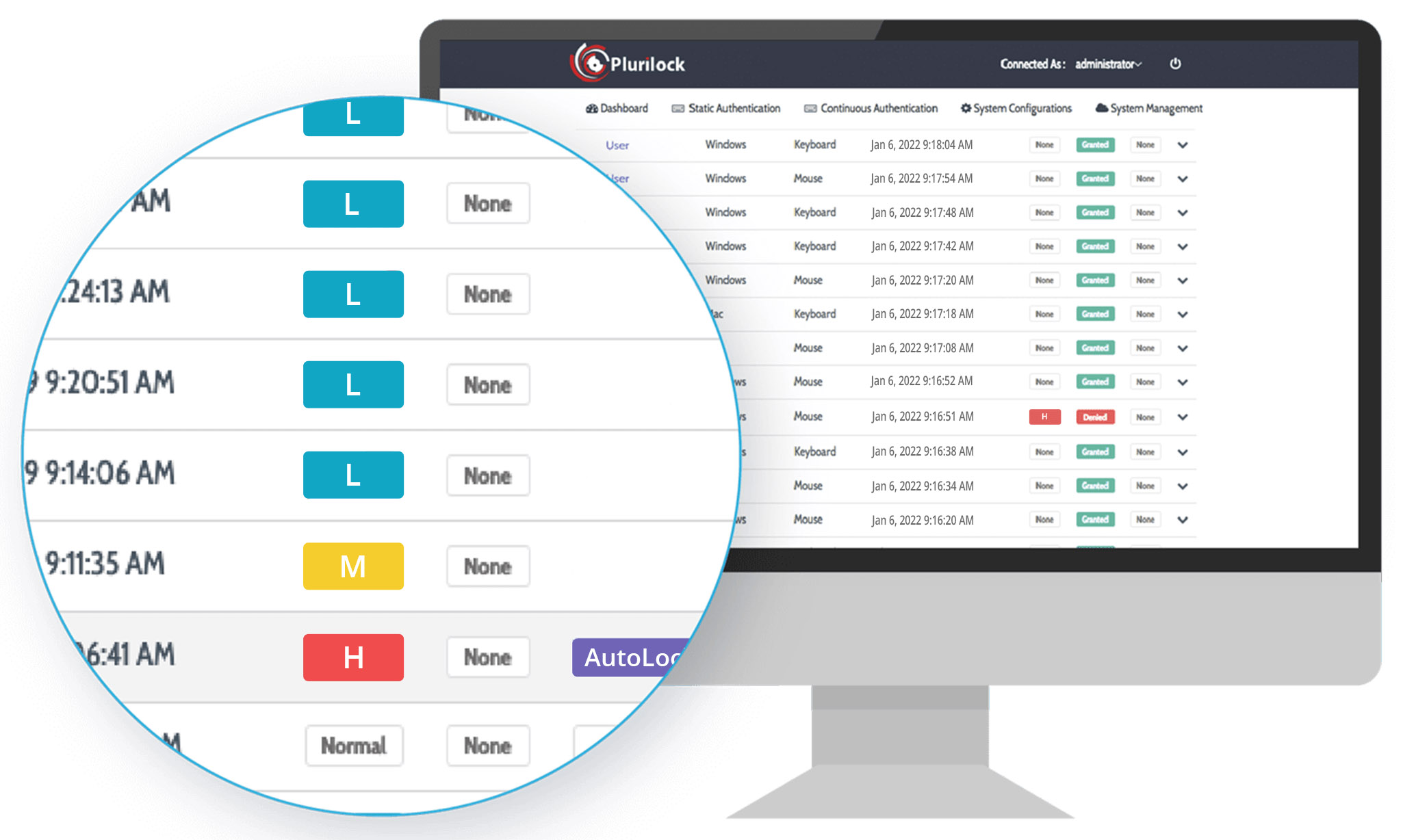
the solution
Plurilock AI Complete with DEFEND™ technology changes the game.

Manage access decisions based not on login identity but on biometric identity confirmed in real time, as work happens.

Remove access immediately any time the user at the keyboard changes or a session is stolen, even if tokens are valid.

Control who can use, share, or modify cloud data, and what can be stored there, all with real-time identity certainty.

Prevent local data use entirely or ensure that data only goes to the right endpoints—with the right users actually at them.
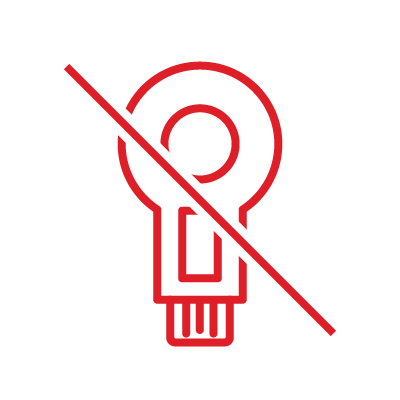
Full-day biometric identity every 3-5 seconds for access, cloud, and data policy decisions—without any new hardware.
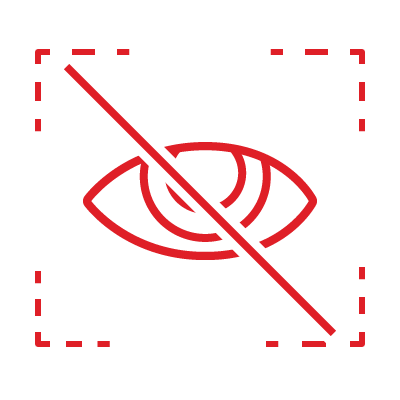
Achieve least privilege, zero trust, and full identity awareness and SIEM data enrichment without affecting user work.
How it Works
Cloud-era SSO, CASB, and DLP meet award-winning behavioral biometrics.
Plurilock AI Complete combines comprehensive cloud-ready SSO, CASB, and DLP capabilities with Plurilock’s patented DEFEND™ technology to unlock true least privilege and zero trust.
Policy decisions can be made based on real-time identity, not session tokens hours old, and SOC events can be directly correlated to actual people, regardless of the credentials in use.

A lightweight endpoint agent tracks user keyboard and mouse movement patterns and enforces CASB and DLP policies

Plurilock’s AI-driven cloud engine analyzes movement continuously, confirming identity and applicable policies

Grant and deny decisions can be made based on real-time identity and risk levels, not login identity and stored tokens

Keyboard and pointer motion is analyzed as work occurs. When movements don't match a worker's usual patterns, DEFEND takes action.
Why It's Different
True trust elimination.
Legacy cybersecurity platforms use login identity as the core of the decision-making process and the primary key for event logs—but login identity trusts credentials and MFA devices.
Plurilock AI Complete with DEFEND™ technology provides least privilege access management, CASB, and DLP tied to users and their presence in real time—eliminating trust in credentials, devices, and tokens.
Why It's enterprise-ready
Scalable and privacy-friendly.
The Plurilock AI Complete machine learning engine runs on a cloud server designed for fault tolerance and high availability to ensure nonstop identity verification—all workday long.
Even better, the DEFEND™ technology underlying Plurilock AI Complete relies only on simple keyboard and pointer motion—not link clicks or text—so your data remains secure.
Where It Works
Broad compatibility. Environment-level deployment.


Plurilock AI Complete
SSO, CASB, and DLP with real-time AI identity.
Base access and policy decisions on the user at the keyboard now—not an hours-old login token.

+1 (888) 282-0696 (USA West)
+1 (908) 231-7777 (USA East)
+1 (866) 657-7620 (Canada)
Advanced cybersecurity and Zero Trust
Security assessments and consulting
IT products and solutions
Professional services
Managed services






