Reference Materials and Resources
Guidance and Recommendations
Sample, shareable addition for employee handbook or company policy library to provide governance for employee AI use.
Generative AI is exploding, but workplace governance is lagging. Use this whitepaper to help implement guardrails.
Cheat sheet for basics to stay secure, their ideal deployment order, and steps to take in case of a breach.
Learn about the risk credential compromise poses for your organization.
Prepare your organization for cybersecurity challenges and the new normal.
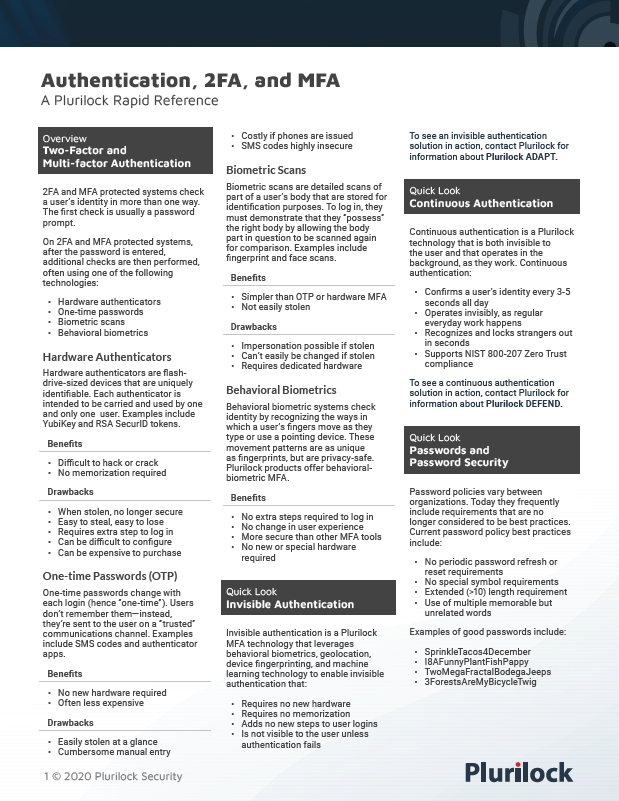
Concise rapid reference to 2FA, MFA, password best practices, and authentication vocabulary.
Detailed Plurilock™ recommendations for password policies, along with the reasoning behind them.
Summary of authentication recommendations from major standards bodies, plus Plurilock's™ own recommendations.
The state of authentication today—and why you need Plurilock™ products.
Product Information
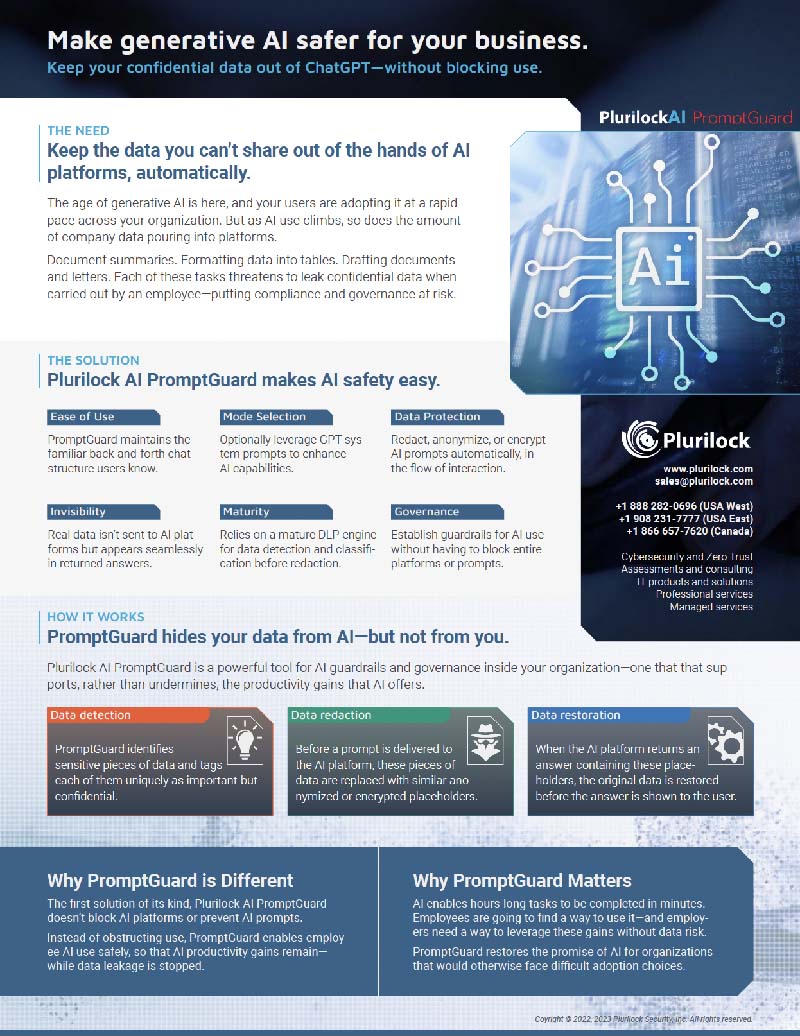
PromptGuard detects and hides confidential data from AI—but not from the user—to provide guardrails for AI use.
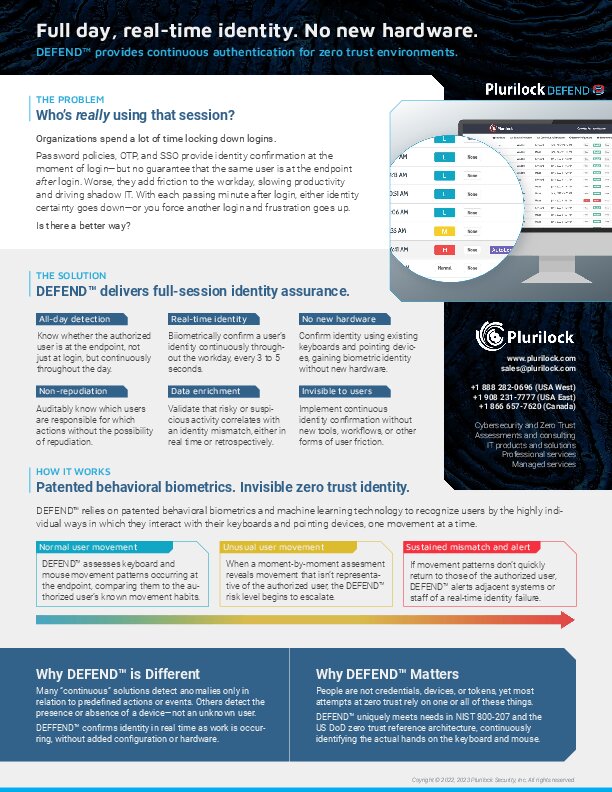
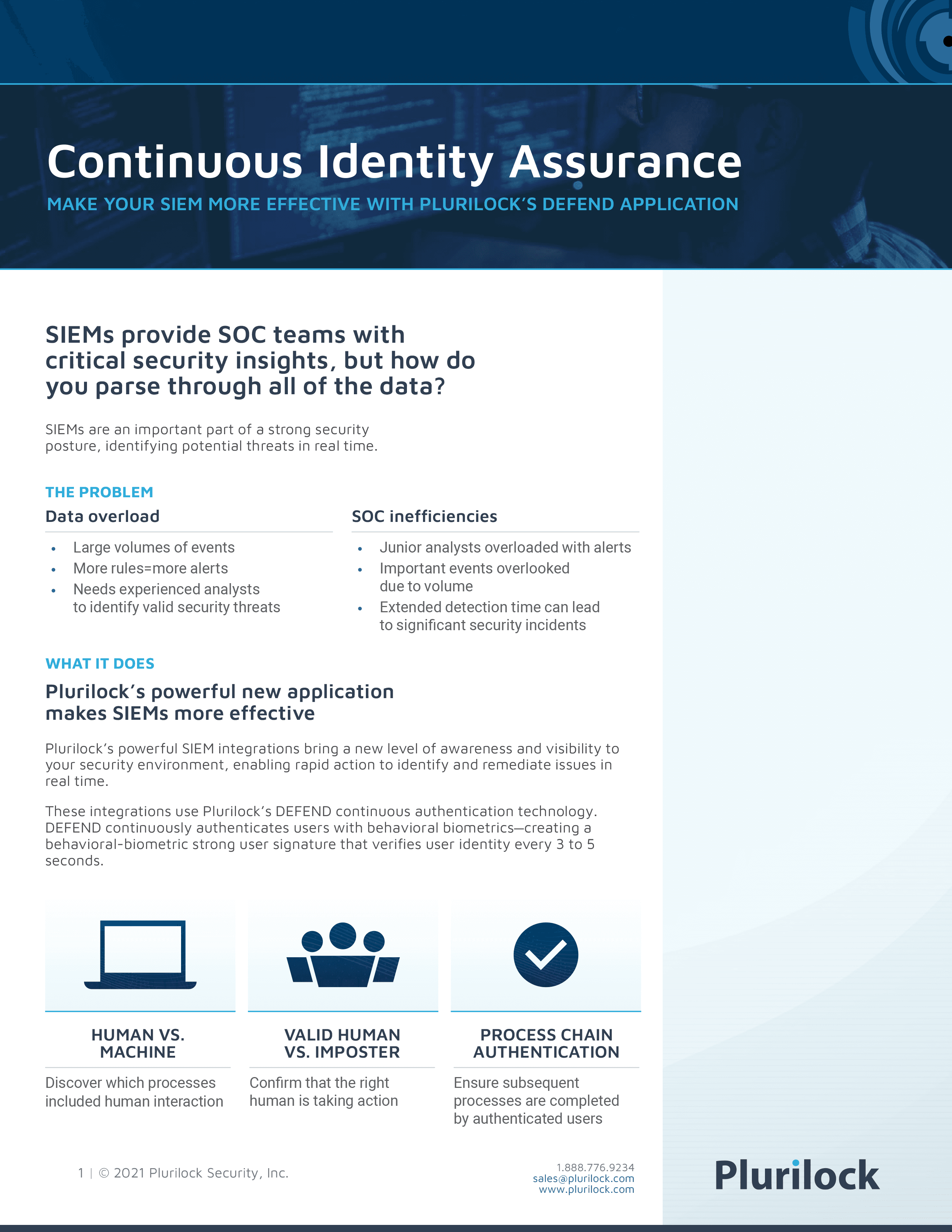
Real-time, continuous authentication using behavioral biometrics and machine learning.
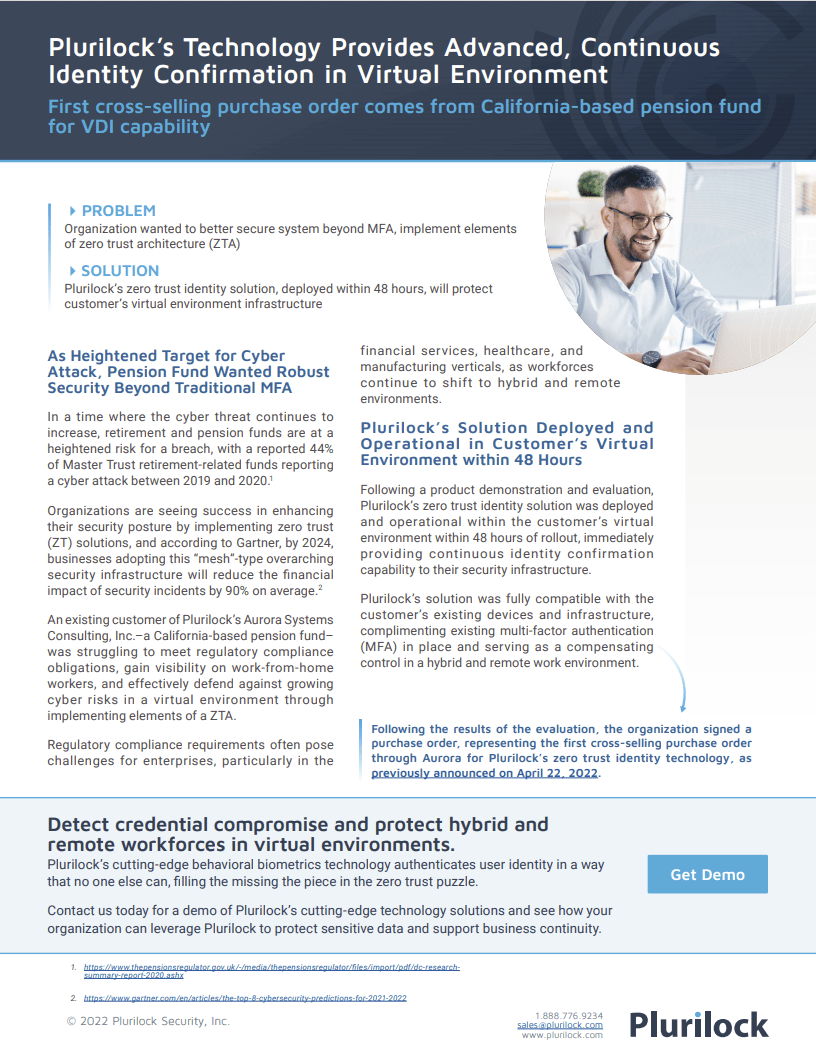
Learn about how Plurilock offers advanced, continuous identity assurance for virtual environments.
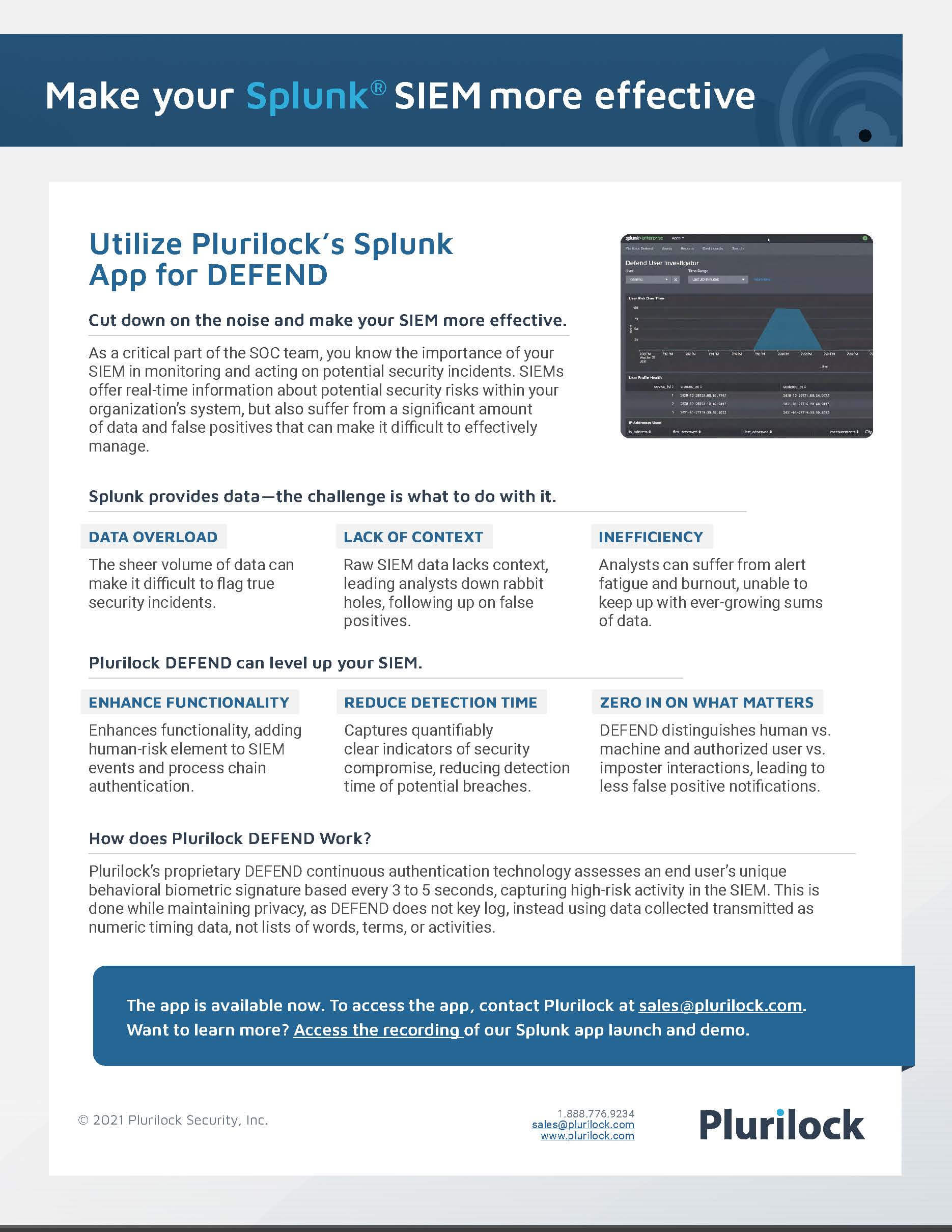
Learn how Plurilock’s DEFEND app can level up your Splunk® SIEM
Learn how SOCs can utilize Plurilock’s Splunk® App for DEFEND.
Plurilock ADAPT and DEFEND use behavioral biometrics and ambient identity signals to confirm identity, not just credential validity.
Join forces with Plurilock as your Zero Trust technology partner. Here's why.
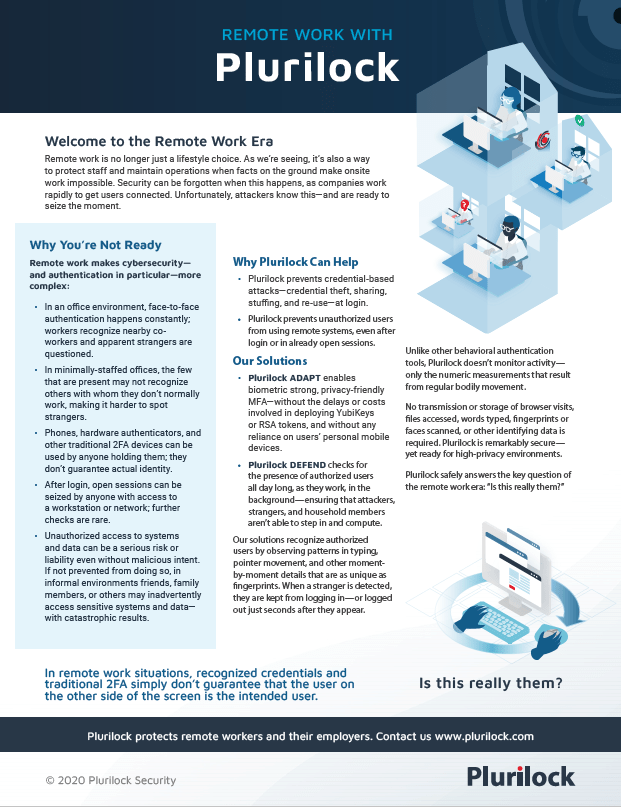
The work-from-home era is upon us—and Plurilock enables security without frustrating staff or overloading support.