Critical Services Datasheets
From penetration tests and phishing assessments to urgent digital transformation in geopolitical hotspots, Plurilock has you covered.
Plurilock’s Application Security Assessment ensures compliance with industry regulations and identifies vulnerabilities through comprehensive testing, enabling robust protection for your critical applications.
Plurilock’s Cybersecurity Risk Assessment employs comprehensive methods to evaluate and enhance your security posture, providing actionable insights for regulatory compliance and risk mitigation.
Plurilock’s Data Classification Technical Assessment provides insights into data organization, access patterns, and potential risks, enabling proactive measures for enhanced security.
Plurilock’s HIPAA Security and Compliance Audit offers comprehensive assessments to ensure healthcare organizations meet regulatory standards, prioritize vulnerabilities, and optimize security practices.
Plurilock Critical Services offers expert consulting and support for comprehensive networking and security solutions, empowering businesses to navigate and thrive in the dynamic cyber threat
Plurilock’s PCI DSS Gap Analysis ensures thorough identification of security gaps, streamlining compliance efforts and mitigating risks effectively.
Plurilock’s Penetration Testing delivers comprehensive evaluations of IT environments, identifying vulnerabilities through simulated attacks for enhanced security.
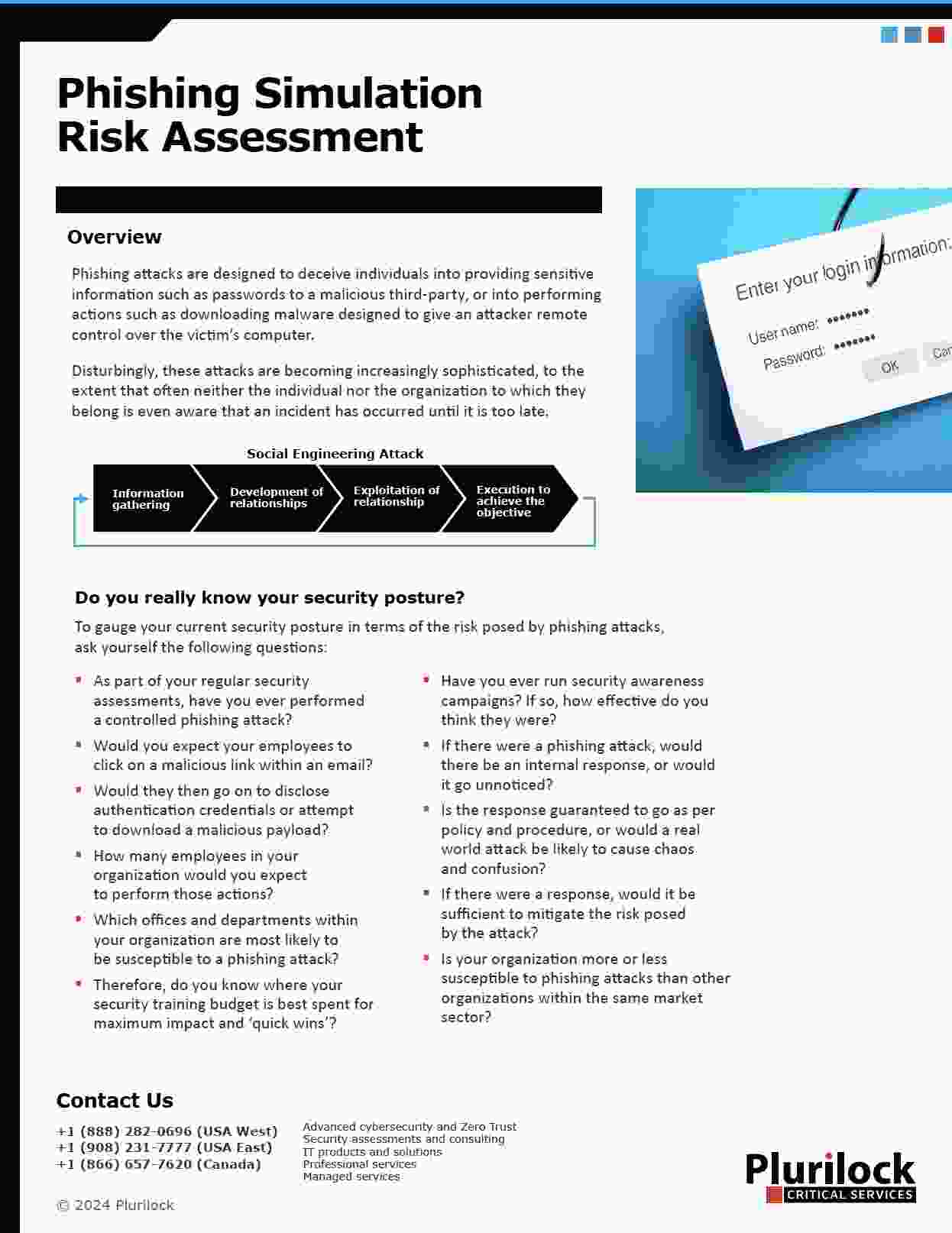
Plurilock’s Phishing Simulation Risk Assessment provides a thorough evaluation of your organization’s susceptibility to phishing attacks, enabling targeted mitigation strategies.
Plurilock Critical Services offers expanded cybersecurity capabilities through strategic partnerships and acquisitions, providing state-of-the-art solutions for comprehensive protection and business success.
Plurilock’s Security Code Review employs a blend of automated tools and manual analysis to mitigate risks, enhance compliance, and optimize costs.
Plurilock’s Vulnerability Assessment offers tailored methodologies for efficient risk mitigation, automated scanning, and cost-effective compliance, enhancing organizational security.