Behavioral Biometrics
What it is, where it came from, and why it matters
The Answer to Today’s Cyber Threats
Every day, new threats appear. Old security practices are slowly failing; new technologies are required to thwart attacks. The most promising of these is behavioral biometrics—a revolutionary, privacy-friendly method for authenticating users that is transforming the security industry.
You’ve probably encountered traditional biometric authentication already in smartphone fingerprint readers and face scanners. You’ve probably also heard concerns about traditional biometric technologies and their implications for privacy and safety—as well as some of the ways in which they can be fooled.
Behavioral biometrics takes the strengths of traditional biometrics technologies and eliminates the weaknesses and concerns that surround them. It does this by ending the reliance on body parts or records of activity, instead analyzing unique micro-patterns in movement—patterns that are unique, impossible to duplicate or fabricate, and that can’t be used to reconstruct a person’s identity or biography—only to authenticate them.
But how does it work? And what does this technology mean for your business or organization?
This guide is designed to show you.
Let's get started.

We generally advise a layered, orchestrated and risk-adjusted approach, combining passive methods, such as device profiling and behavioral biometrics, with traditional data.”
Aaron Press, Director, Market Planning, Fraud, and Identity, Lexis Nexis


Chapter 1
What is Behavioral Biometrics?
2017 marked an all-time high for global cyberattacks, with nearly 160,000 incidents reported—almost double the 2016 count of 82,000.1 This trend shows no signs of slowing. By 2021, costs related to cybercrimes such as identity theft will reach a staggering $6 trillion annually.2
In today’s world of increasingly sophisticated cyberattacks, traditional authentication methods—including multi-factor methods based on SMS, mobile identity, or authenticator apps—are not strong enough. Organizations increasingly need state-of-the-art cybersecurity measures that provide persistent, adaptive authentication while simultaneously reducing expensive administrative headaches and user friction.
Enter Behavioral Biometrics
Behavioral biometrics defined:
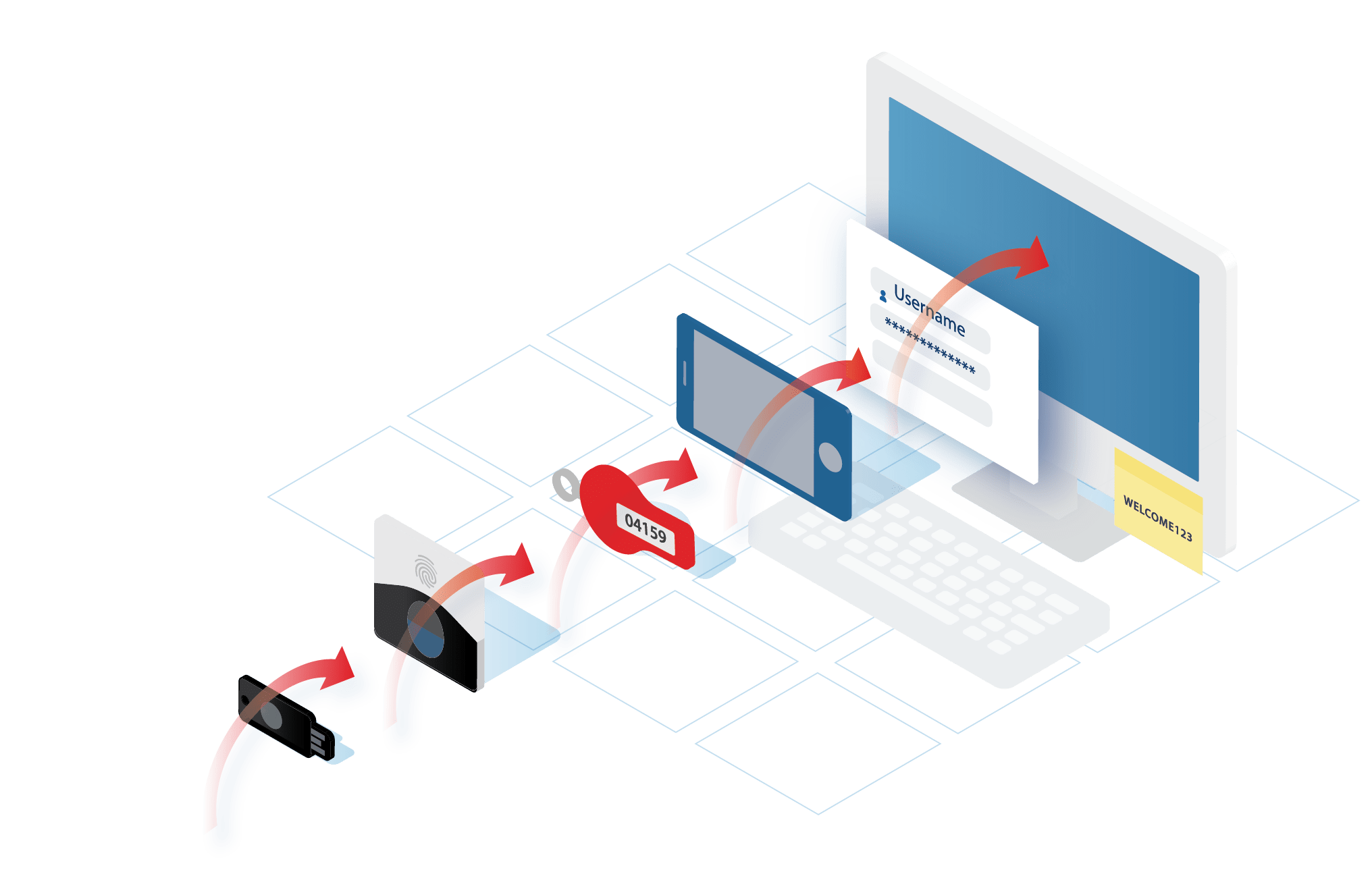
Behavioral biometrics is an evolving technology that authenticates users based on patterns in their behavior. It identifies unique, individual regularities in the ways that people type and move, rather than identifying parts of their bodies (fingerprints or irises), things that they have (key fobs or phones), or things that they know (passwords or biographical details).
Unlike traditional authentication methods, which authenticate only when access is initiated, behavioral biometrics technologies authenticate continuously, evaluating a user’s ongoing interaction with their computer in real time.
But how does it work?


How it works:
Every person behaves in a completely individual way. The gait with which someone walks, the fluctuations in vocal tone as they speak, and the cadence with which they type are as unique as fingerprints—but are much harder for malicious actors to capture, much less duplicate. Behavioral biometrics uses these patterns to authenticate users and protect data.
Plurilock’s™ behavioral biometric tools run on the actual mobile devices and computer systems connected to an organization’s data. Each user with valid access automatically generates a behavioral profile that reflects the distinct ways in which they interact with critical systems—gestures such as keystrokes, and mouse movements. Once a user’s profile is learned, their gestures are monitored silently, in real time, to continuously authenticate identity. If behavioral patterns that don’t match the profile occur, the system can immediately prompt for other forms of authentication, block access, or lock the device down entirely. At present, behavioral biometrics is best seen as a powerful, non-overlapping addition to other forms of authentication. In the future, as behavioral biometrics matures, it will likely replace other authentication methods entirely.3- Protects from attacks when malicious users gain administrative privileges
- Offers firmware-embedded architecture for self-healing capabilities
- Provides better protection than other OS-level application protection


Neat. Well, what kinds of behavioral biometrics exist today?
Types of Behavioral Biometrics
Though the field of behavioral biometrics continues to evolve, three basic types of behavioral biometric data can already be identified: kinesthetics (body movements), vocal patterns, and device-based gestures.
Device-Based Gestures

Keystroke Dynamics: Typing patterns that vary uniquely from user to user. These include a combination of keystroke speed, keystroke duration, variations in these for particular key sequences, and characteristic patterns that occur when typing common groups of keystrokes such as words or control sequences.
Cursor Movements:Unique patterns in mouse or trackpad cursor movement including paths, tracking speed, direction changes, clicks, and the relationships between these.
Body Movements

Voice Inputs
Posture: The unique properties of an individual’s body position and weight distribution while standing or while seated.
Gait: An individual’s unique walking style, including characteristic movements made while in motion: stride length, upper body posture, and speed of travel relative to these.

Vocal Patterns: The unique, regular variations in sound that occur as a user speaks or vocalizes.
Behavioral vs. Physiological
Behavioral biometrics tools differ in key ways from less secure physiological (body-based) biometrics tools.
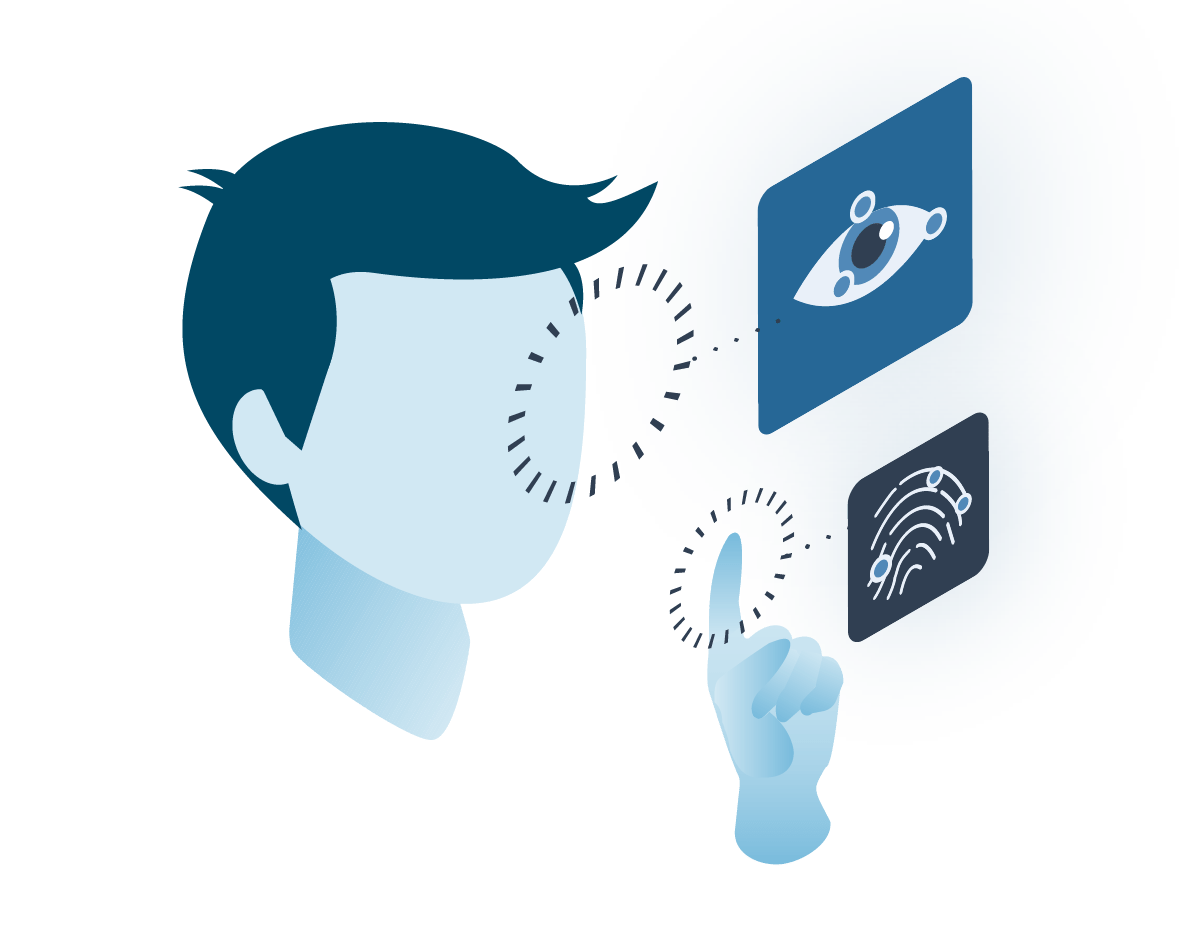
Physiological
Physiological biometrics relies on the structures of the body for identification—for example, on fingerprints, on facial dimensions, or on the parts of the eye. Though these structures make each individual body unique, they are static, which leaves them more vulnerable to being scanned or photographed, then reconstructed for malicious use.

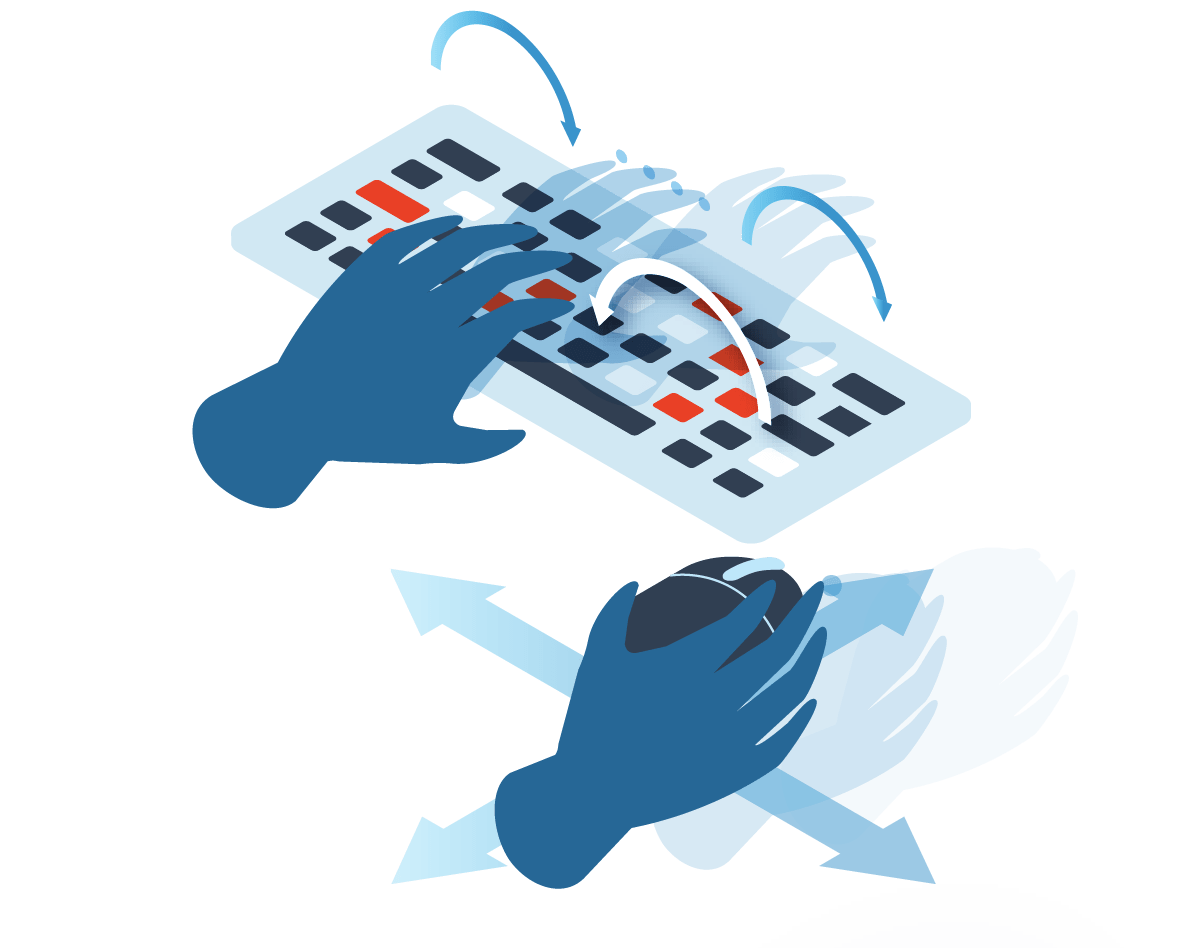
Behavioral
Behavioral biometrics identifies patterns in the ways that particular bodies perform particular tasks—patterns in walking, speaking, typing, or even mouse behavior. These patterns are prohibitively difficult to capture and replicate, and they evolve over time.
Behavioral biometrics tools profile these patterns, then evolve with the user. They leverage powerful statistical models and machine learning to spot the differences between a known user’s gradual evolution and the unwanted presence of an entirely different user.

Makes sense, but what can behavioral biometrics do?
Behavioral Biometrics Use Cases
No matter what countermeasures are in place, login credentials are periodically stolen or compromised. This endangers systems, data, and entire infrastructures. Behavioral biometrics can be used to ensure that the person attempting to use a system has been legitimately granted access to it.
The informal sharing of named accounts is a common security risk. Best-in-class behavioral biometrics technologies can differentiate between intended users and everyone else—even as login credentials are being entered—and block authentication accordingly.
Ad-hoc substitution of one user for another, without prior knowledge or consent, is both common and risky, particularly in outsourced environments. Behavioral biometrics algorithms can ensure that the person actually using a system is the person presumed to be using it.
Oversights in privileged access management can give rise to internal threats—users whose access to some systems inadvertently results in access to others. Behavioral biometrics can ensure that the actual moment-by-moment use of any system is carried out only by intended users.
Oversights in privileged access management can give rise to internal threats—users whose access to some systems inadvertently results in access to others. Behavioral biometrics can ensure that the actual moment-by-moment use of any system is carried out only by intended users.
USB-based attacks commonly rely on rapid, automated data entry simulating keyboard or mouse use. Whatever the human user’s understanding of or reaction to the attack, behavioral biometric tools are not fooled; they can immediately note the change in input patterns and block further input.
Though behavioral biometrics can’t stop a user from clicking on malicious links or supplying sensitive data to malicious actors, it can rapidly detect intruders that use phishing data to access and act on a secured system—no matter what they attempt to do once logged in.
If attacks or breaches occur, behavioral biometrics can be used to identify internal participants in them. The biometric signature of the actions taken can be compared against known user profiles, identifying the culprit(s) using the nuances of their keyboard or mouse behavior.
Even the most conscientious users may inadvertently leave workstations unattended or unlocked before stepping away. Behavioral biometrics can identify the arrival of a new, unauthorized user rapidly—even at an unlocked workstation—and take appropriate measures.
The illicit sharing of per-seat licenses is both common and a liability risk for many large organizations. Behavioral biometrics can ensure that licensing practices are sound and only named users make use of licensed products and services.
Financial services organizations, health care organizations, or others that provide services to end-users can rapidly profile each user’s behavior and stop malicious attempts to access data or services with stolen user credentials.

Click title to read more about each use case.
Passive,
Pervasive MFA
Passive and pervasive by design, behavioral biometrics is a completely invisible link in the authentication chain. Behavioral biometrics is transparent and frictionless; until threats arise, users don’t even know it’s there.
High Regulatory Compliance
Behavioral biometrics tools enable organizations to meet key portions of the increasingly stringent cybersecurity standards and regulations set forth by NIST 800-171, ISO 27001, HIPAA, FINRA, and FISMA.
Chapter 1 References
- Online Trust Alliance: Cyber Incident & Breach Trends Report. Review and analysis of 2017 cyber incidents, trends and key issues to address. Retrieved June 12, 2018. See: otalliance.org
- CyberSecurity Ventures: Cybercrime Damages $6 Trillion By 2021. Retrieved June 12, 2018. See: cybersecurityventures.com
- National Institute of Standards and Technology. July 2018. Digital Identity Guidelines Authentication and Lifecycle Management.

What's the history of Behavioral Biometrics?
Chapter 2
From Morse Code to Keyboards
A brief history of key events and developments in behavioral biometrics
1940s
Morse code authentication
in WWII
The earliest form of behavioral biometrics dates to World War Two. During the war, Allied forces became adept at recognizing one another based on individual signaling patterns, using these to authenticate sensitive messages.
1959
Machine learning
gets its name
Artificial intelligence pioneer Arthur Samuel gives this name to a theoretical computer’s ability to learn on its own, without human intervention—a capability that would someday become critical to behavioral biometrics.
1960s
First model of acoustic
speech production
MIT Drs. Gunnar Fant and Kenneth Stevens first model speech production using x-rays of speaking subjects. Their findings are the first suggest a link between behavior—in this case, speech—and individual biology and identity.
1970
Behavioral components
of speech mapped
Dr. Joseph Perkell creates an early form of biometric modeling using full-motion x-rays and the previous work of Drs. Fant and Stevens. This work would eventually lead to the biometric voice recognition tools still in use today.
2001
Sept 11th and continuous
authentication1
In a now highly-networked world, the the September 11th, 2001 attacks on the World Trade Center draw attention to the need for continuous authentication as a new security measure in global information systems.
2002
Data mining and
biometrics converge
The U.S. Defense Advanced Research Projects Agency (DARPA) launches Total Information Awareness (TIA), the first large-scale use of technologies designed to mine data sets for identifying biometric information.
2006
Early Plurilock research
A University of Victoria team develops innovative new algorithms that rapidly and transparently identify computer users as they work. This team will later become Plurilock, and the algorithms will later be patented.
2012
DARPA launches active
authentication program
In pursuit of increased security across devices operated by the U.S. military, DARPA launches the Active Authentication (AA) program—the first widespread application of behavioral biometrics authentication.
Plurilock is Founded



2006–2016
After 35,000 hours of research, development, and algorithm refinement by top Ph.D scientists (who literally wrote the book on Behavioral Biometrics) Plurilock emerges as a major player in the authentication scene.
2016–Present
Plurilock is officially founded and launches its DEFEND and ADAPT products using now patented algorithms to bring continuous authentication to highly-regulated environments like government, critical infrastructure, financial services, and healthcare.
Chapter 2 References
1. Traore, D., and Ahmed, A. 2012. Continuous Authentication Using Biometrics: Data, Models, and Metrics.
Chapter 3
You Are the New Password
Behavioral biometrics and authentication today
Passwords have long been the standard authentication tool. But there are a growing number of serious problems with this form of authentication.
Users today have a lot of passwords to remember—more than ever before—and they’re asked to change them frequently. Each of these passwords can be used by anyone that has them if they’re compromised or stolen.
Meanwhile, the need for ever more complex passwords, in ever greater numbers, that are ever more ready at hand leads to poor password hygiene and habits. These defeat the purpose of password use.


How do password managers change things?
What about password managers?
For these reasons, multi-factor authentication (MFA) is now in widespread use. By requiring both a known password and the possession of a particular device or other hardware, MFA is designed to plug some of the holes that decades of password use has created.
But devices, too, are vulnerable to loss, social engineering, and theft—often at the same time that passwords are being stolen—and MFA makes heavy demands on users and support teams.


Behavioral biometrics, on the other hand, plugs these holes by providing invisible authentication that is neither password- nor device-dependent.
Instead, everyday behavior provides continuous, real-time verification of identity, whatever device is being used. Meanwhile, strangers are caught and excluded—with or without the “right” passwords and devices.

Let's see how behavioral biometrics stacks up.
Password Problems
A closer look at how current authentication methods perform
Passwords
Vulnerability
HIGH
Prone to human error, poor hygiene, and theft.
User Friction
HIGH
Forgetfulness and complex password policies lead to high support needs.
Regulatory Compliance
LOW
Does not alone meet many current regulatory standards.
MFA
Vulnerability
MEDIUM
Prone to human error, and compromised
by device loss or theft.
User Friction
HIGH
Forgetfulness and complex password policies lead to high support needs.
Regulatory Compliance
HIGH
Behavioral Biometrics
Vulnerability
VERY LOW
The capture and re-use of micro-behaviors is currently not possible.
User Friction
NONE
Regulatory Compliance
HIGH
Chapter 4
Considerations in Applicability
Caveats to note when deploying behavioral-biometric solutions
Behavioral Biometrics Requires Systems Use
Behavioral biometrics enables authentication based on unique user behavior profiles. These are initialized when users engage with and use secured systems. In rare cases, however, exceptionally infrequent or irregular use may slow profile creation.
Users that interact with secured systems briefly and only once or twice per year, for example, may produce very little behavioral data.
In these cases, alternate authentication methods must be used until sufficient data about the user’s behavior can be gathered to enable behavioral-biometric identification.


Microbehavior—Not Activity—is Profiled
Thanks to the Cambridge Analytica scandal, GDPR1 and similar regulations, and rising press coverage, concerns about user privacy have become key policy concerns. For similar reasons, fraud prevention measures that definitively identify users before granting access to data are becoming increasingly essential. Plurilock’s behavioral biometrics solutions meet both of these needs, without requiring complex workarounds or exceptions.
Plurilock profiles consist of data used only to match real-time behavior to a profile of past behavior—data that, if found elsewhere, could not be tied to any real person.
What users do is not stored; only patterns of microbehavior (how keys were pressed, how mice were moved) are represented in each profile.

Chapter 5
The field of behavioral biometrics is growing rapidly. Enabled by advances in computing power, behavioral biometrics is moving from the lab to the corporate or governmental office. Who’s involved and what’s the value of the industry now?
Let's take a look.

The Industry Today
Two types of companies are in the behavioral biometrics business today: we’ll call them “pure plays” and “incorporators.”
Pure plays vs. Incorporators

Pure Plays like Plurilock offer behavioral biometrics technologies as a core product, and are focused on building and offering these technologies. Pure plays have been the driving force behind the scientific and business growth of behavioral biometrics in recent years.
Plurilock was born from this kind of focused, groundbreaking work, led in 2006 by current management team member Dr. Issa Traore and research partner Dr. Ahmed Awad E. Ahmed at the University of Victoria.1

Incorporators provide or employ the behavioral biometrics technologies that pure plays develop, usually as part of a larger product or service. They choose to deploy behavioral biometrics because it enables their business or organizational purposes.
One very prominent incorporator is DARPA, the well-known U.S. government research agency responsible for the development of the Internet. DARPA now relies on behavioral biometrics as a key dimension of its organizational security model (see below).
The DARPA Active
Authentication Program
The U.S. Defense Advanced Research Projects Agency (DARPA) was a major force behind the initial growth of behavioral biometrics, which paved the way for companies like Plurilock to perfect the technology.
DARPA’s pioneering Active Authentication (AA) Program, launched in 2012, sought to enhance security across the US military by complementing traditional authentication methods like passwords with behavioral biometrics approaches.
The two phases of DARPA’s AA roll-out led to findings and refinements that have been critical to the widespread—and still growing—adoption of behavioral biometrics technologies.

Cool. Let's talk about machine learning.
AA PHASE I: User analysis
In this phase, DARPA conducted a far-reaching analysis of behavioral traits in computation. These included keystroke patterns and mouse movements.
AA PHASE II: Technology, development, and implementation
In this phase, DARPA used its Phase I findings to develop a new tools capable of validating users’ identities based on computational-behavioral traits.

Machine Learning and the Growth of Behavioral Biometrics
Big data has been a growing obsession in science, government, and business for over a decade now. Global networks, billions of mobile devices, and a new “internet of things” have produced unprecedented amounts of data that humans alone could never hope to analyze or understand. Artificial intelligence, which enables computers to analyze and make use of this data, has exploded as a result.
The subfield of artificial intelligence research known as “machine learning” has been a key enabler in the continued growth of behavioral biometrics.
Machines that learn are able to astutely refine or enhance their own capabilities as they perform key tasks or encounter data related to these tasks—just what’s needed for behavioral biometrics technologies to “learn about” user behavior and gradually evolve with it over time.
The advances in machine learning that have occurred over the last decade have thus resulted in a seismic shift in behavioral biometrics—taking it from a largely research-oriented field to a portfolio of market-ready technologies ideal for use in industry.
Filling the Gap: Customer Experience Meets Cybersecurity
Today’s customers expect smooth experiences that are free of complications or stumbling blocks. Brands that do this well succeed, those who fail may lose business. Along with user experience, cybersecurity is a hot topic— awareness is at an all-time high. Password-based and two-factor authentication methods are currently industry standard, and while these reassure some customers, they interrupt the sales process for many others who turn away in frustration.
In other words, the current practices in cybersecurity and user experience design are at odds with one another. Behavioral biometrics is increasingly being used to fill this gap—by adding a secure, data-driven authentication layer that adds no friction to users’ experiences.
Behavioral biometrics
and the employee experience
Think of your employees as internal customers. They experience the same frustrations balancing security and ease of use but, while a customer may only have infrequent interactions with the brand, employees are interacting with the systems daily. Being able to protect their endpoints without added “hoops to jump through” keeps employees happy and reduces helpdesk burden, improving efficiency and security at the same time. Behavioral biometrics can add this additional, invisible layer of security, letting employees get on with their work.
Behavioral Biometrics is used in many different industries, in a variety of ways. From protecting customer-focused web applications, to making sure it’s really you accessing your savings account, to protecting the workplace against insider threat, behavioral biometric tools allow businesses to scale and automate their authentication processes.
Like this.

Customer-focused web application protection
Exclusively static authentication

Identity Assurance for the Workplace
Only Plurilock continuously authenticates users in the workplace, verifying user identity every 3-5 seconds. This kind of behavioral biometrics, with refined, mature, and patented algorithms, bridges the gap that many other cybersecurity products leave behind. It protects the endpoint for the entire session, not simply a webpage or app.

Plurilock benefits
for continuous authentication
Plurilock’s unique stack of invisible authentication factors identifies actual people as they work, not just their logins and passwords, all day long.
Protect corporate endpoints sessions invisibly, as users work. Authentication doesn’t end after login. It’s continuous—and goes on until logout.
Plurilock’s light-weight endpoint agent runs continuously and invisibly on PC and Mac.
Detect threats instantaneously. Respond to unauthorized use at machine speeds, eliminating admin-busy lag.
Plurilock’s adaptive factor stack tracks micro-patterns in behavior, environment, and context.
Verify multiple identity factors without conspicuous intrusions, interruptions, or additional steps.
Harden your application against identity threats without slowing down clients, apps, browsers, or real work.
Achieve the protection of MFA with the hardware you have—no phones, fobs, codes, or tokens needed.
Plurilock benefits
for cloud and web apps

Chapter 5 References
1. Traore, D., and Ahmed, A. 2012. Continuous Authentication Using Biometrics: Data, Models, and Metrics.
Chapter 6
Forecast for the Future of Behavioral Biometrics
Prediction 1
Adoption will continue to increase.
The first wave of behavioral biometrics solutions to see marketplace adoption was focused on mobile computing. While these applications remain essential, over the next several years behavioral biometrics will become a significant security paradigm in non-mobile computing contexts as well.
Adoption of behavioral biometrics technologies will continue to increase across organizations of all types—to meet the the growing need for highly secure authentication that balances increasingly stringent privacy, security, and user experience quality requirements.
Prediction 2
Generalized anomaly detection is next.
By 2020, some 26 billion devices will be connected to the “Internet of things” (IoT). Ranging from personal and household devices to sensitive military and scientific equipment, these units represent a vast ocean of vulnerability spread throughout human environments—for which device-by-device password authentication is implausible.
Behavioral biometrics is now coming to the fore in authentication practices. In the future, anomaly detection technologies inspired by behavioral biometrics will proliferate as an ambient security platform for IoT devices, too.
Prediction 3
Cybersecurity will become proactive.
As AI and machine learning continue to advance, their ability to draw conclusions, learn from, and take intelligent action based on real-time data inputs will also grow.
In the years to come, these advancements will drive even greater predictive and adaptive capabilities for behavioral biometrics technologies—for example, the ability to predict and correct user mistakes based on past behavior, or the ability to preemptively allocate or deallocate network and computing resources based on previous patterns of legitimate use.
About Plurilock