Plurilock’s™ powerful Splunk integration brings a new level of awareness and actionability to your security environment, enabling rapid action to identify and remediate issues in real time.
Ingest DEFEND Risk Data with Splunk
Pull DEFEND’s continuous authentication data into Splunk and use powerful Plurilock tools to analyze and act on this data.
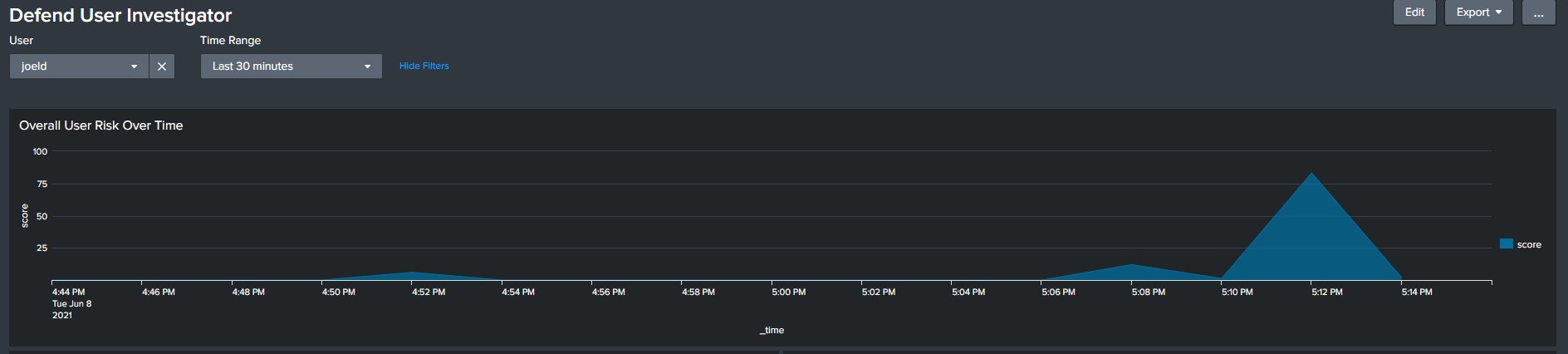
Easily Identify Compromise and Risk Events
See compromise events and periods of credential misuse and impersonation clearly, from the beginning of the event to its end.
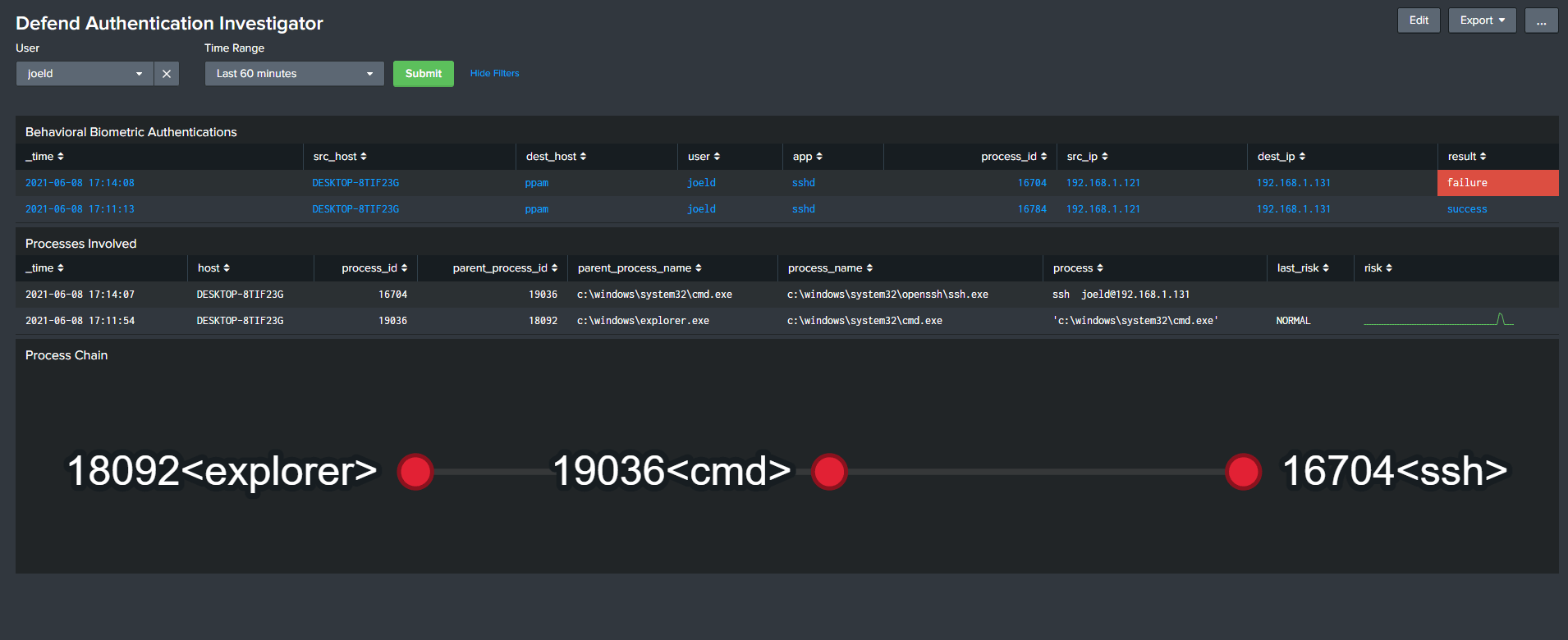
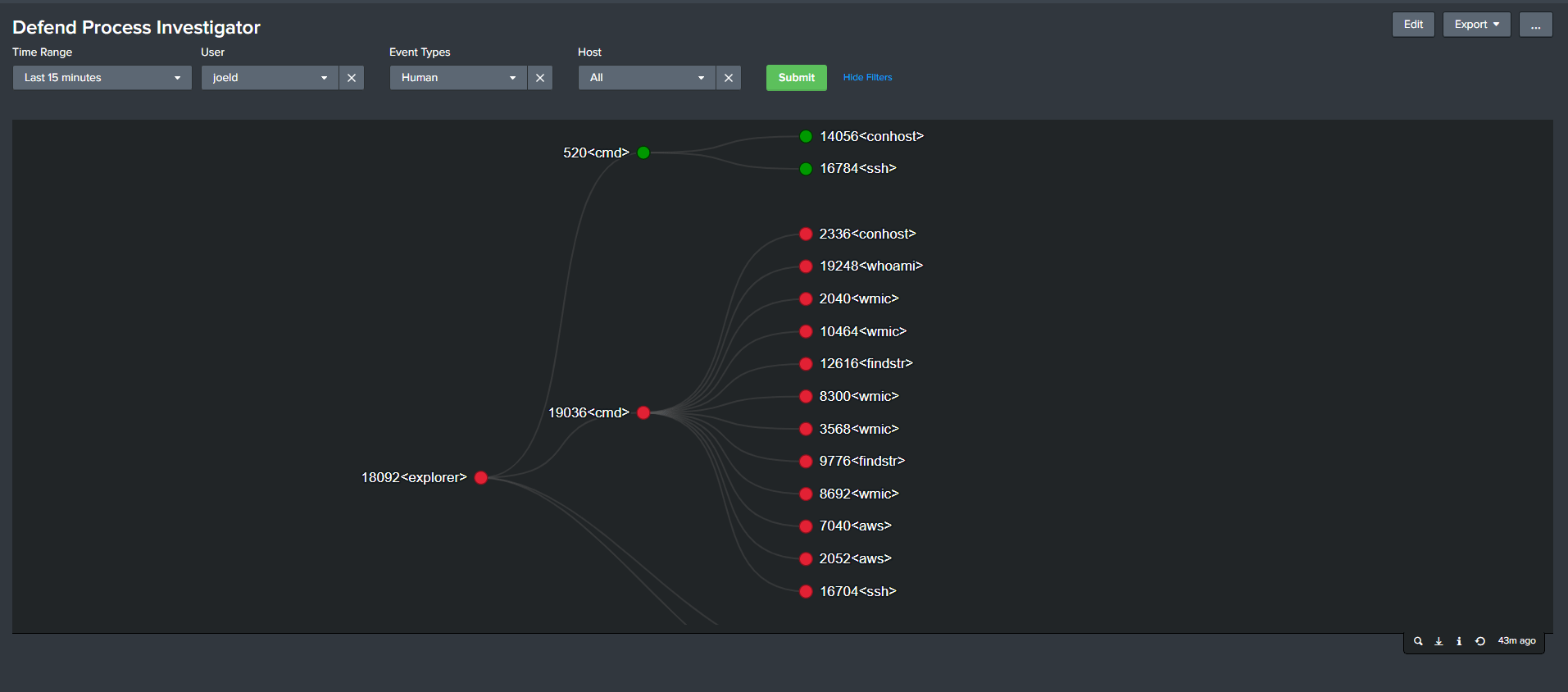
IDENTIFY BAD PROCESSES, SEE Just What Matters
Automatically filter out non-interactive processes and rapidly chart which processes were carried out by the attacker, line by line and process by process.