Zero trust has been a long-known concept within the cybersecurity industry but has not, until recently, trickled out into the larger vernacular. Following several high-profile breaches like Colonial Pipeline, JBS Meats, and Kaseya, and increased geopolitical friction with cyber attacks sponsored by nation-states, there has been a renewed call for solutions like zero trust that can protect networks from the growing cyber threat. Earlier this year, U.S. President Biden issued an executive order (EO), calling for enhanced protections for federal agencies, fostering partnerships with the private sector to improve the nation’s security posture, and establishing standardized criteria for a zero trust architecture (ZTA).
Plurilock’s™ cutting-edge cybersecurity solutions address critical elements of the larger zero trust puzzle, as outlined in the guidance document from NIST.
What is zero trust?
Zero trust is the concept that you can “trust no one” in your network infrastructure, even those working internally for an organization; a departure from the concept of using firewalls to keep external threats out but trusting those within the system.
Critical elements of a ZTA also include:
-
The ability to authenticate transactions based on identity, context, and risk
-
The ability to authenticate transactions before access is given and continuously afterward without added user friction
-
The ability to access resources from any platform, so long as the transaction is fully authenticated
Zero trust removes some of the burden on the employees to navigate cybersecurity policies in a time of increased remote work, with clear guardrails that can flag compromised credentials before disaster strikes. According to Centrify, to combat poor security practices from employees, 57% of business decision-makers revealed that they are currently implementing additional authentication measures as a result. In a true ZTA, these risks would be largely mitigated.
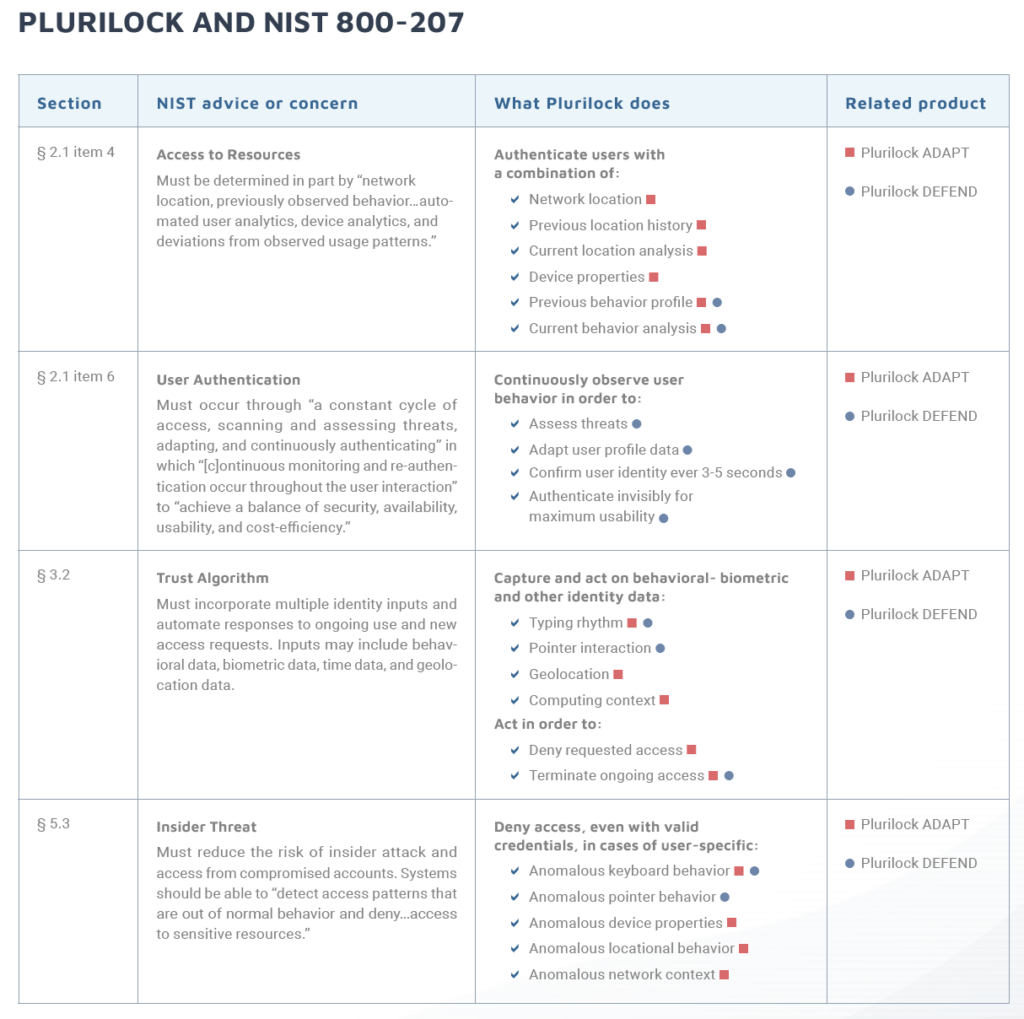
While a standardized criterion for a ZTA is being established, the U.S. National Institute for Standards and Technology’s (NIST) Special Draft Publication 800-207 serves as the primary guidance document, outlining fundamental requirements for achieving zero trust.
Per the document, an organization protects resources by defining existing resources, who its members are (or its current ability to authenticate users), and what access to resources those members need. In a ZTA, client identity can include the user account (or service identity) and any associated attributes assigned by the enterprise to that account.
In essence, this portion of the guidance focuses on privilege access management, defined as the restriction of access rights and permissions for users, accounts, applications, systems, devices, and computing processes to the absolute minimum necessary to perform routine, authorized activities. The more privileges and access a user, account, or process amasses, the greater the potential for abuse, exploit, or error. Implementing privilege management as part of a ZTA minimizes the potential for a breach occurring and limits the impacts.
Plurilock’s cutting-edge behavioral biometrics cybersecurity solutions address critical elements of the NIST guidance:
Plurilock ADAPT™
Plurilock ADAPT is a standards-based login MFA platform that provides an additional, invisible authentication factor using behavioral biometrics while reducing two-factor authentication (2FA) prompts. This offers protection against stolen-credential attacks without the need for fingerprint scans, SMS codes, hardware tokens, or other legacy MFA requirements.
Plurilock ADAPT spots and stops illicit credential use, aligning with zero trust elements, including the assessment of:
- Network location
- Previous location history
- Current location analysis
- Device properties
- Previous behavior profiles
- Current behavior
Plurilock DEFEND™
Plurilock’s DEFEND is a continuous authentication platform that offers identity assurance and compromise detection, alerting IT security personnel to potential threats in real time. The platform runs invisibly, providing continuous identity detection and endpoint visibility in the background as users work.
Plurilock DEFEND continuously analyzes user micro-patterns to confirm identity, aligning with zero trust elements, including the assessment of:
- Previous behavior profiles
- Current behavior
The Right Level of Trust
Plurilock is the missing piece of the zero trust puzzle, with cutting-edge cybersecurity solutions that offer identity assurance and continuous authentication elements fundamental to building a ZTA. By incorporating Plurilock’s ADAPT and DEFEND solutions into a ZTA, your organization can establish the “just right” level of trust.
Disclaimer
The NIST’s SP 800-series publications are guidance documents. They should not be interpreted as altering or superseding the existing authorities of the Secretary of Commerce, Director of the OMB, or any other federal official.
















