
Passwords, SMS codes, email links, even fingerprints and face scans—all of these kinds of credentials can be stolen and re-used by people other than their original owners.
Plurilock’s true continuous authentication technology recognizes users based on tiny patterns in their keyboard and mouse movements—patterns that can’t be detected or reproduced by human observers, but that Plurilock’s machine learning engine can spot immediately.

Passwords, SMS codes, email links, even fingerprints and face scans—all of these kinds of credentials can be stolen and re-used by people other than their original owners.
Plurilock’s true continuous authentication technology recognizes users based on tiny patterns in their keyboard and mouse movements—patterns that can’t be detected or reproduced by human observers, but that Plurilock’s machine learning engine can spot immediately.
Lots of products claim to offer “continuous authentication” yet only authenticate users on a periodic basis. Let’s be real—periodic authentication is not continuous. It just isn’t.
Plurilock’s true continuous authentication technology never stops authenticating users, even as they are doing other work. Plurilock's continuous authentication technology confirms user identities every 3-5 seconds, in the background, throughout the workday.
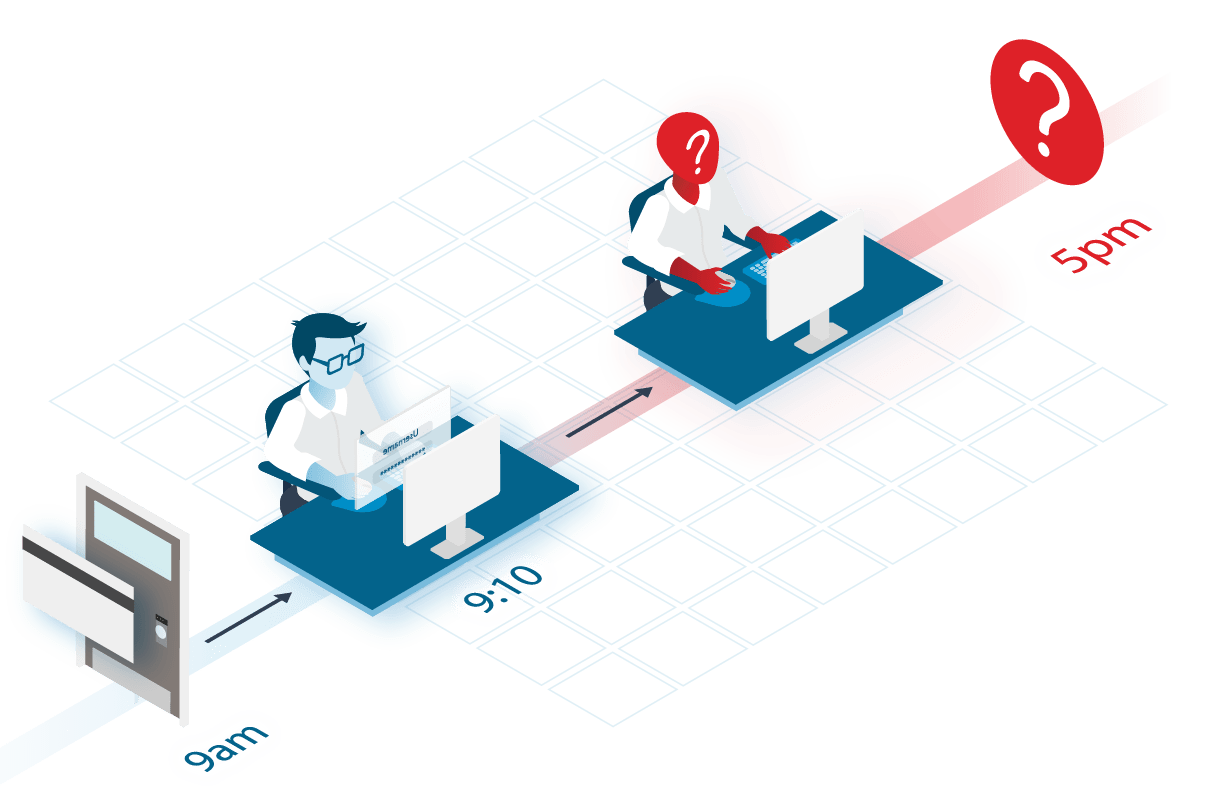

Most data breaches happen when unauthorized employees access access other users’ accounts and sessions.
They do this by stepping in when authorized users forget to log out—or by nabbing and using credentials that they shouldn’t have.
Plurilock’s true continuous authentication technology eliminates these threats. If the wrong user tries to use a session or account, even if it’s already logged in, access is ended—just like that.
NIST Special Publication 800-207 calls for true continuous authentication as a key ingredient in the achievement of zero trust environments.
This means MFA that operates continuously, confirming real identities every few seconds in the background, all day long—and that ends access once identity can no longer be confirmed.
Who has a true continuous authentication like this? Plurilock does.

Copyright © 2024 Plurilock Security Inc.