23.65Percent | Estimated compound annual growth rate (CAGR) for the passive authentication market from 2018-2028.https://www.mordorintelligence.com/industry-reports/passive-authentication-market |

The sheer number of authentications required of users today can lead to frustration and loss of productivity. Passive authentication is meant to solve this.
As technology—and especially the cloud—become more and more a way of life, authentication has come to take up more and more of the average person's time. This is true both in the lives of employees and in peoples' private lives after hours.
Sometimes it seems as though getting anything done is an endless set of authentication steps, so that it takes minutes or even hours to get started on nearly any task as you try to complete all of the authentications needed to start all of the software needed to begin.
Passive authentication is one possible answer to this problem.
The goal of passive authentication is to find a way to confirm identity—and thus a way to ensure secure computing—that doesn't require the user to take any particular concrete steps. Examples of passive authentication include technologies like behavioral biometrics and some forms of camera-based face identification (for example, when positioned above a laptop screen).
These technologies can simply "look at" the user and decide whether or not they should be authenticated—without the user having to stop and type things in, look things up, place a finger somewhere, provide a code, or do anything else that takes time. Instead, authentication happens (for the user) in a "passive" way.
Because it takes time to do all of these things, passive authentication is generally a way to accelerate all of the authentication steps that a user would otherwise have to perform, reducing the total time they dedicate to authentication from minutes or hours down to seconds, and also a way to eliminate friction that might ultimately negatively affect a user's work, or perceptions of the software, or that might even cause them to give up on beginning a task at all.
 Need Passive Authentication solutions?
Need Passive Authentication solutions?Plurilock offers a full line of industry-leading cybersecurity, technology, and services solutions for business and government.
Talk to us today.


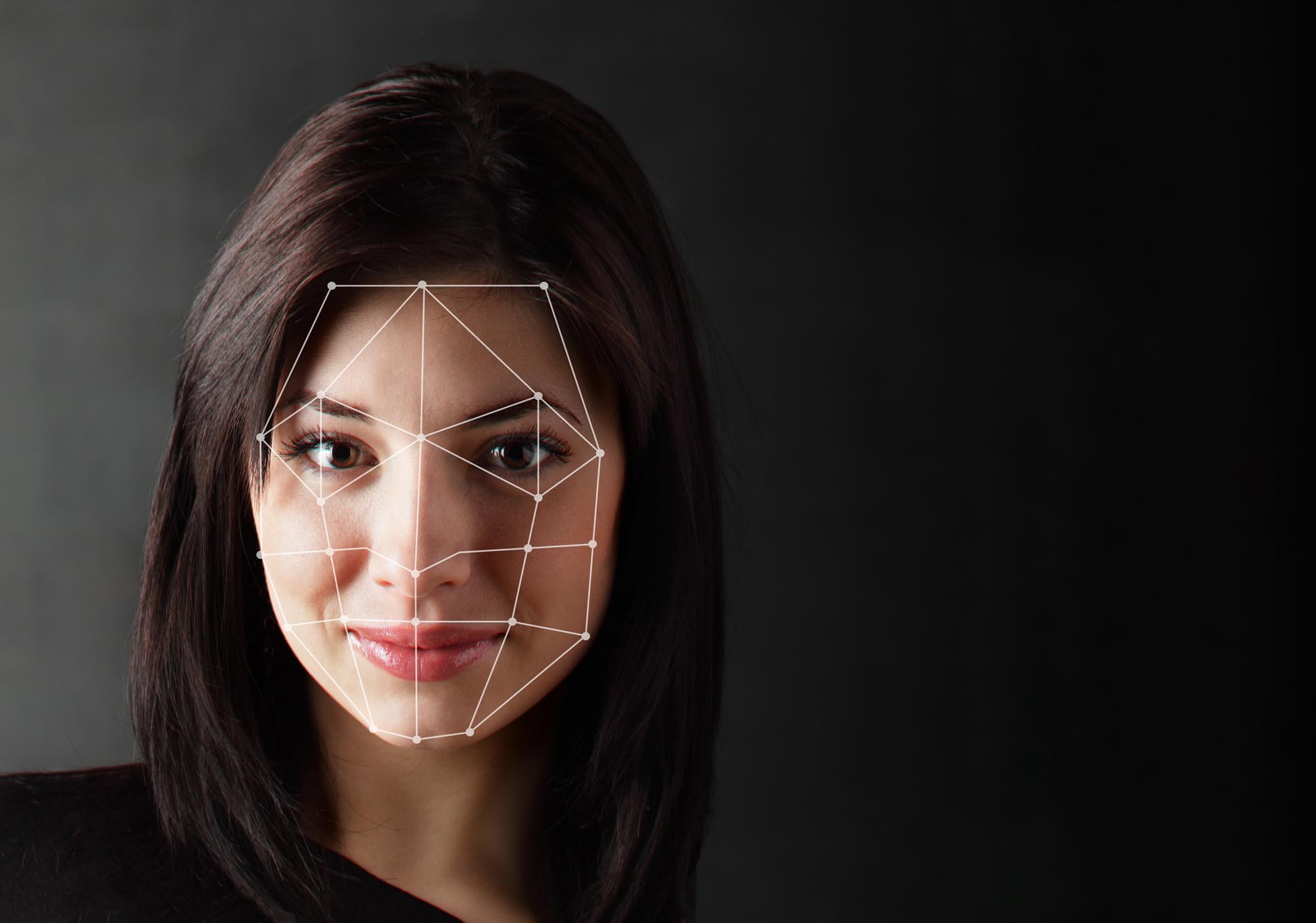
Passive Authentication is a form of authentication in which the identity of the user is checked and confirmed without requiring specific additional actions for the purpose of authentication. Instead, the user's activity, properties, or other observable data are gathered and analyzed for evidence of identity without additional intervention from, or work by, the user. Passive Authentication is, in essence, frictionless.
The invisible MFA technology in Plurilock ADAPT is a form of passive authentication, added to existing login prompts, that adds multiple additional identity verification factors without requiring additional steps from the user. Instead, identity signals are gathered as they perform the usual entry of their username and password, enabling much stronger identity confirmation without addition work from the user.
Copyright © 2025 Plurilock Security Inc.