Authentication2019
Authentication
2019
Why IT Matters

COMPROMISED CREDENTIALS
Four out of every five recent breaches resulted from compromised credentials. (Centrify)
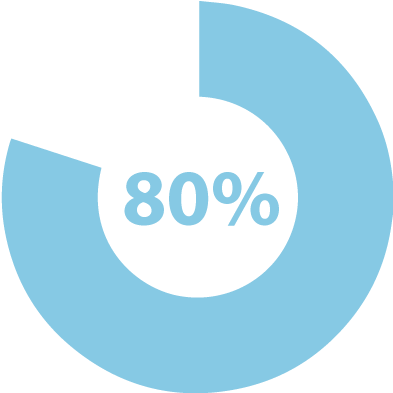
INADEQUATE AUTHENTICATION
Better multi-factor authentication could have prevented 80 percent of breaches. (Symantec)
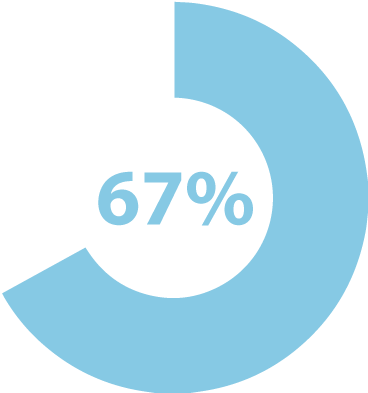
BUSINESSES ATTACKED
Over the course of 2018, two-thirds of all small- and medium-sized businesses experienced cyberattacks. (Ponemon)

GLOBAL CYBERCRIME DAMAGES
By 2021, global damages from cybercrime will will reach $6 trillion—twelve times the value of the global trade in illegal drugs. (Cybersecurity Ventures)
trying to fix it
Multi-factor authentication (MFA) is the best defense against ongoing threats.
With MFA you can log in only after providing something that you have or are in addition to something that you know.
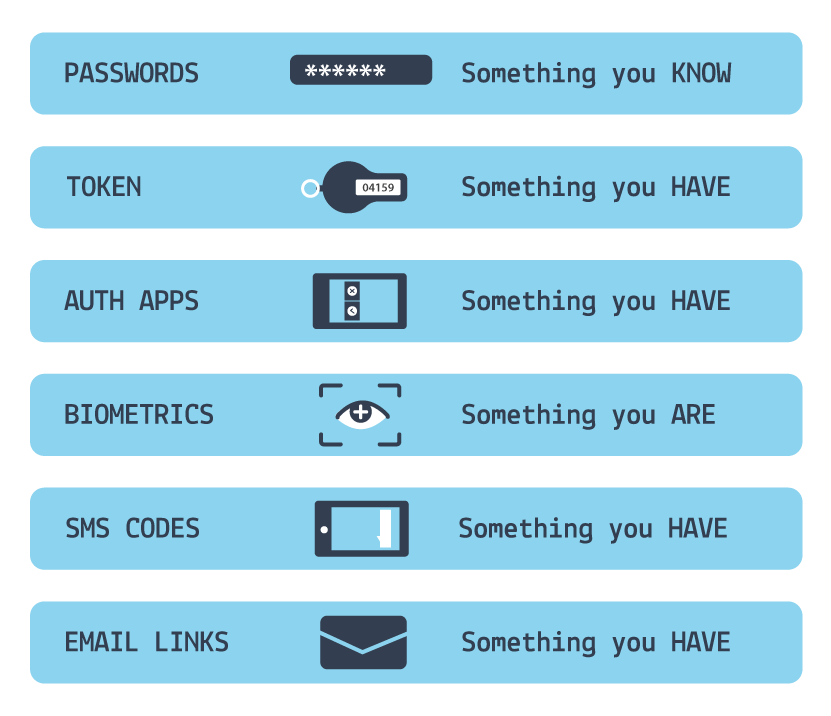
Multi-Factor Authentication:
Pick 2+

Something You Know
✓ Passwords
✓ Passphrases
✓ Shared secerets

Something You Have
✓ Hardware token
✓ Mobile phone
✓ Common access card

Something You Are
✓ Fingerprint
✓ Facial structure
✓ Behavior and habits
MFA? Consensus.
Passwords? Not so much.
Standards bodies agree on the need for MFA and strong passwords.
They disagree on how to maximize password strength.
Password
Character Rules


NIST 800-63

ISO 27001
27002

PCI DSS
_
OWASP

GCHQ NCSC

Plurilock
Password
Auto-Expiry


NIST 800-63

ISO 27001
27002

PCI DSS

OWASP

GCHQ NCSC

Plurilock
Passphrases


NIST 800-63
_
ISO 27001
27002
_
PCI DSS

OWASP

GCHQ/ NCSC

Plurilock
Secret Security
Questions


NIST 800-63
_
ISO 27001
27002

PCI DSS

OWASP

GCHQ NCSC

Plurilock
SMS Codes
In-band MFA


NIST 800-63
_
ISO 27001
27002

PCI DSS

OWASP

GCHQ NCSC
_
Plurilock
True Out-of-band
MFA


NIST 800-63

ISO 27001
27002

PCI DSS

OWASP

GCHQ NCSC

Plurilock
why authentication is complicated

The Easy-Hard Problem
Passwords that are hard to crack are also hard to remember and enter.
Passwords that are easy to remember and enter are also easy to crack.
The IN-BAND Problem
SMS and apps, the two leading MFA tools, may deliver credentials to the same device being authenticated.
The COPY-NO-CHANGE Problem
Fingerprints and face scans have proven to be easier to duplicate than initially imagined, yet can't be changed once compromised.
Each conventional factor
has strengths and weaknesses
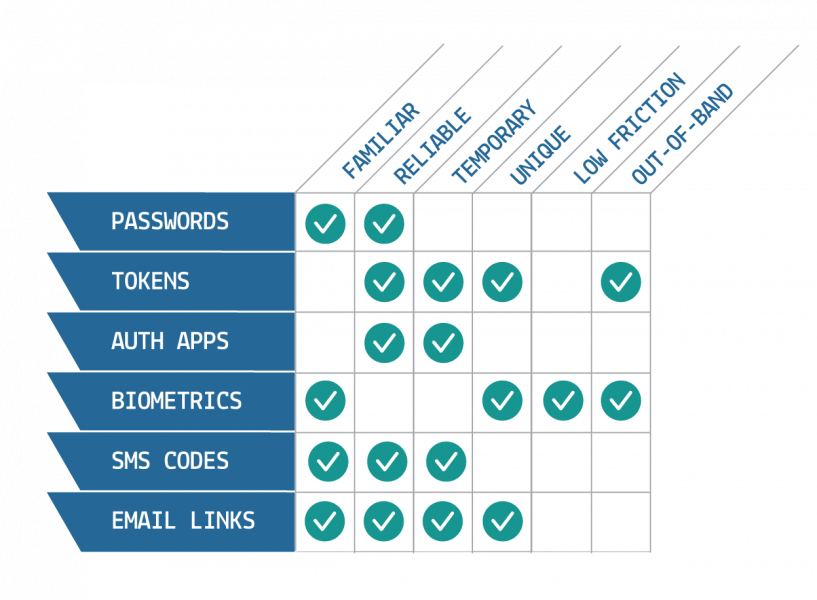
strengths
of common MFA factors
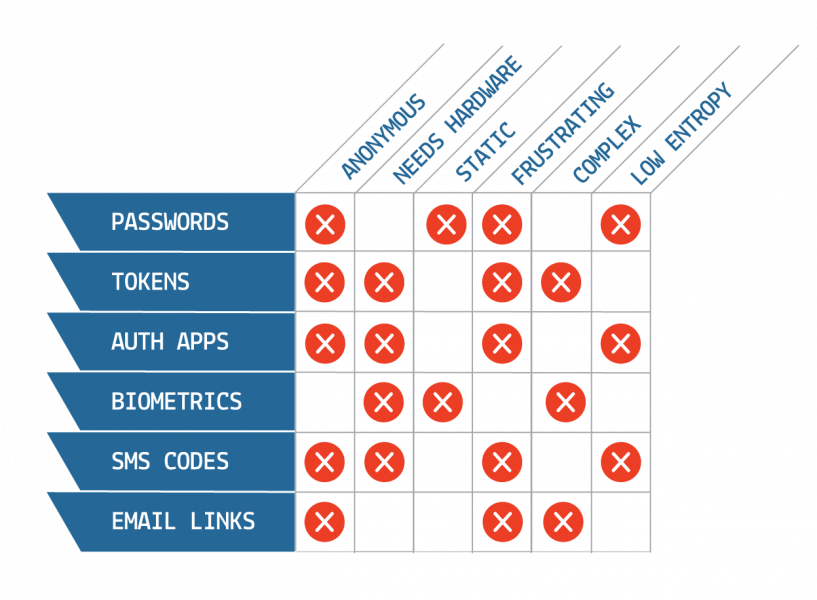
Weaknesses
of common MFA factors
The industry's Next Step:
a composite that combines them
advanced authentication
leverages conventional MFA concepts in new ways.
Keystroke
Dynamics
Pointer
Dynamics
Geolocation
+ Movement
Device
Fingerprint
Network
Context
Time
of Day
Keystroke
Dynamics
Pointer
Dynamics
Geolocation
+ Movement
Device
Fingerprint
Network
Context
Time
of Day

This composite authentication strategy adaptively evaluates any available identity factors all at once.
This is what we do at Plurilock.
2019 Authentication recommend-ations From Plurilock
Use 2+ Identity
Factors

Something a user Knows
A password or passphrase.

Something a user has
A mobile phone or hardware token.

Something a user Is
User behavior or traditional biometric data.
Make Passwords Better
LONG
Each additional character exponentially increases security.
UNIQUE
Avoid a breach domino effect by using a new password for each account.
MEMORABLE
A list of random words is easier to recall than random characters or numbers.
Choose High-Quality, Out-of-Band Factors
Acceptable
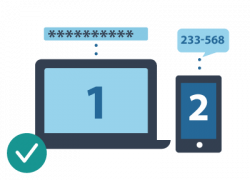
Password entry on laptop +
Authenticator app on mobile phone
Acceptable

Password entry on mobile phone +
fingerprint scan on mobile phone
Not Acceptable

Password entry on
mobile phone +
SMS code delivered to
mobile phone
These guidelines represent the minimum baseline for secure authentication.









