Identity and Access Management (IAM or IdM)

In the increasingly interconnected digital landscape, the importance of safeguarding sensitive information and maintaining secure access to resources cannot be overstated. Identity and Access Management
Attribution

In the ever-evolving landscape of cybersecurity, one concept stands out as both crucial and elusive: attribution. At its core, attribution seeks to uncover the digital
Data Exfiltration

Latitude Data Breach

Remote Access Trojan (RAT)

Identity Threat Detection and Response (ITDR)

Credential Stuffing

In today’s interconnected digital landscape, cybersecurity has become a paramount concern for individuals, businesses, and organizations. One of the most prevalent and concerning threats in
User Behavior Analytics (UBA or UEBA)

Biometric Authentication

Alert Fatigue

Plurilock DEFEND™ – Continuous Authentication with Behavioral Biometrics
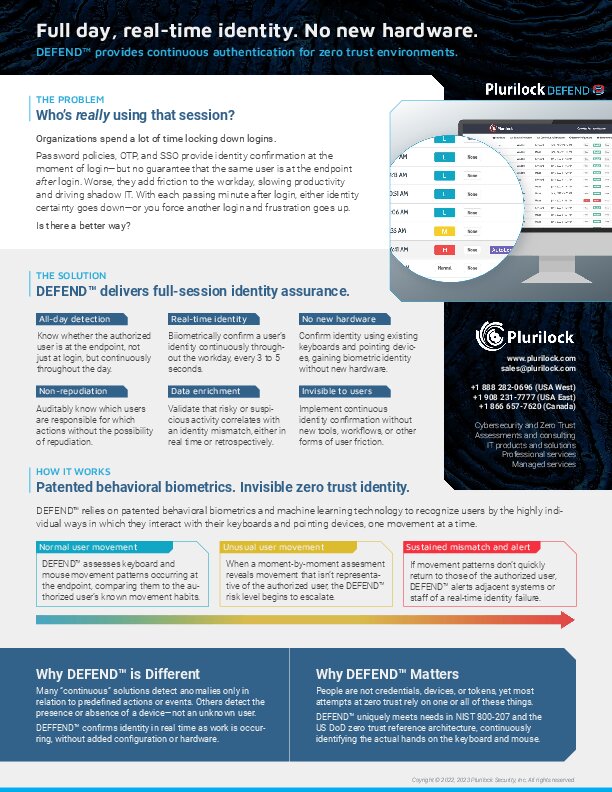
Real-time, continuous authentication using behavioral biometrics and machine learning.








