At their best, hardware tokens offer an alternative to the particular security, convenience, privacy, and cost issues that accompany phone-based multi-factor authentication.
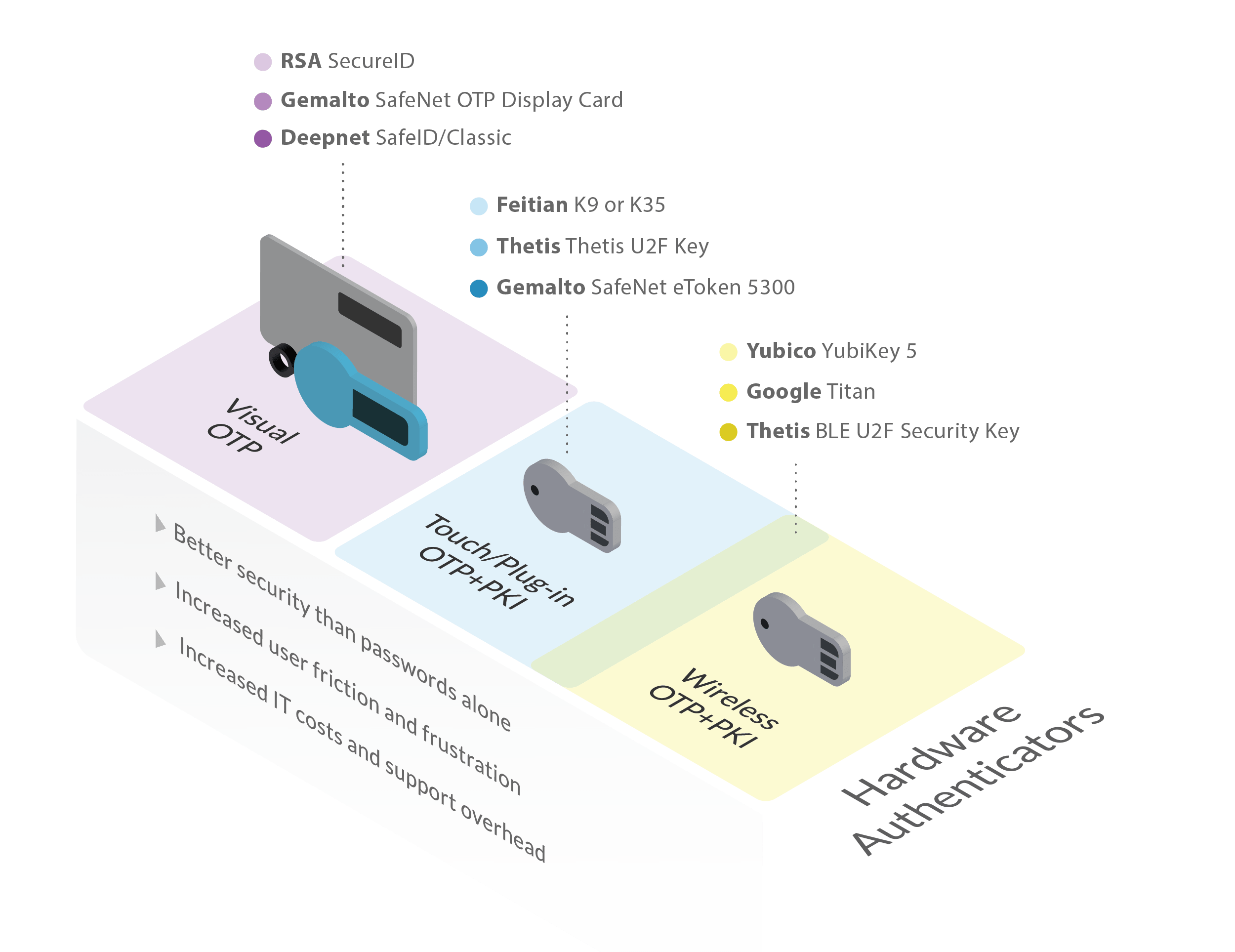
Yet the hardware token landscape can seem confusing—particularly given its mix-and-match nature in terms of features and form factors. Still, look deeper and it becomes clear that there are just three major kinds of tokens on the market:
Visual OTP authenticators. These tokens display a short, rotating one-time password (OTP) on a small screen. In most cases, the user must manually enter this code at the login prompt.
Touch or plug-in OTP+PKI authenticators. Rather than displaying codes, these authenticators type them for you, via USB. That opens the door to far longer OTP codes along with the management and use of public key infrastructure (PKI) and other extended credentials.
Wireless OTP+PKI authenticators. These offer the same credential support as touch or plug-in OTP+PKI authenticators, but supply codes or credentials wirelessly, using either near-field communication (NFC) or low energy Bluetooth (BLE).
We recently took a look at seven of the most popular authenticator families to see just what features they offer and how their back-of-box claims compare. Here's what we found.

Types offered
Form factors
Back-of-box support
Though in the past they have offered hardware tokens in a variety of categories and form factors, RSA's offerings currently come down to two tokens:
RSA SecurID 700
Traditional OTP key fob with code display
RSA SecurID 800
USB OTP fob with code display, credential storage, and automated entry
RSA is in many ways the granddaddy of the token market, offering tried-and-true second-factor authentication.
On the other hand, the short six-digit codes associated with RSA's displays are easy targets for at-a-glance code theft, making the USB versions with long credential storage a better choice.
Factoid: RSA touts the physical robustness of its tokens, saying that they're "designed to withstand the worst imaginable conditions from temperature cycling to mechanical shocks to being immersed in water." This seems overstated, given that the tokens are common plastic with an LCD display.

Types offered
Form factors
Back-of-box support
Gemalto, recently acquired by Thales, offers a wide variety of hardware tokens and authenticators as a part of the SafeNet family:
Visual OTP Authenticators
SafeNet OTP 110; SafeNet OTP Display Card; SafeNet eToken PASS; SafeNet GOLD Challenge Response Token
Touch/Plug-in OTP+PKI Authenticators
SafeNet eToken 5300; SafeNet eToken 5110
Gemalto's PKI/certificate-based tokens offer a hardware token option for those who need PKI features—which go well beyond mere authentication—along with the ability to manage their own key infrastructure.
Gemalto's OTP tokens, on the other hand, suffer from the same basic vulnerability as all short-code OTP tokens—one rapid glance is enough to nab a current code.
Factoid: Gemalto's GOLD Token enhances OTP security by doubling down on OTP. A code provided by the login prompt is used to unlock the token. The token then provides a second code, which the user enters back into the login prompt. More secure perhaps, but also twice the work.

Types offered
Form factors
Back-of-box support
Deepnet actively positions its products as premier solutions for Microsoft Azure MFA and Office 365, as well as for FIDO/FIDO2 applications. They offer a variety of authenticators to fill these roles:
Visual OTP Authenticators
SafeID/Classic; SafeID/Mini; SafeID/Anytime; SafeID/Pinpad; SafeID/Audio; SafeID/Eco
Touch/Plug-in OTP+PKI Authenticators
SafePass/USB; SafePass/NFC
Wireless OTP+PKI Authenticators
SafePass/NFC
Some will no doubt balk at the risks inherent in any wireless authenticator, but this concern should be balanced against the reality that there are currently few viable non-wireless PKI solutions for most mobile devices.
As was the case with RSA and Gemalto, Deepnet's visual OTP tokens are vulnerable to both code and physical theft, making the PKI offerings more compelling when practical.
Factoid: Deepnet's SafeID/Audio OTP token is designed for the vision-impaired and pronounces codes aloud, illustrating the conflicting needs—for example, security and accessibility—that security professionals must regularly balance in the real world.

Types offered
Form factors
Back-of-box support
Yubico's products have two big things going for them. First, they're likely the most widely used hardware tokens in existence, with incredibly broad ecosystem support. Next, none of them use short, displayable codes that are subject to glance-theft or phishing. Their product line is organized into several series:
YubiKey 5 Series
YubiKey 5 NFC; YubiKey 5 Nano; YubiKey 5C; YubiKey 5C Nano; YubiKey 5Ci
Security Key Series
Yubico Security Key; Yubico Security Key NFC
YubiKey FIPS Series
YubiKey FIPS; YubiKey C FIPS; YubiKey Nano FIPS; YubiKey C Nano FIPS
Between the assortment of connectors and sizes on offer, the availability NFC capability, FIPS 140-2 validation, and wide compatibility, Yubico's authenticators support a bigger variety of use contexts than those from any other vendor.
Factoid: Yubico's products are probably the most consumer-friendly hardware authenticators on the market, thanks to a relatively low entry-level authenticator cost, the breadth of software and platform support, and the sheer volume of YubiKey configuration how-tos, videos, and other resources available online.

Types offered
Form factors
Back-of-box support
Like Yubico, Feitian makes authenticators with a wide variety of form factors and connectors. While Feitian notably lacks a Lightning port option, they offer a Bluetooth option that Yubico doesn't. Products include:
Touch/Plug-in OTP+PKI Authenticators
ePass A4B; ePass K10; ePass K12; ePass K21; ePass K28; ePass K39
Wireless OTP+PKI Authenticators (NFC)
ePass K9; ePass K35
Wireless OTP+PKI Authenticators (NFC+BLE)
MultiPass K13; MultiPass K25; MultiPass K32; MultiPass K41
Beyond wireless differences, Feitian's large selection also differs from that of Yubico by way of being less bare-bones, with more polished designs and token appearances—while at the same time lacking a product designed specifically for FIPS compliance.
Factoid: Feitian makes visual customization a selling point for their hardware authenticators, offering many casings and color choices, laser engraving and printing, and swappable faceplates—things that might make them more popular with users, and thus, by extension, IT staff.

Types offered
Form factors
Back-of-box support
Thetis has the simplest and least expensive offering of any product family we considered, and is in many ways at the opposite end of the authenticator spectrum from an enterprise stalwart like RSA. Thetis offers just two authenticators:
Touch/Plug-in PKI Authenticator
Thetis U2F
Wireless PKI Authenticator (BLE)
Thetis BLE U2F
In many ways, the Thetis simplicity is what makes it compelling—a simple product line and a limited focus on FIDO and FIDO2 support. Thetis is appealing to consumers and small companies that just need low-cost, relatively jargon-free support for the most common applications.
Factoid: Remarkably, Thetis tokens are among the only tokens we looked at that have a traditional USB flash drive appearance, and that fold away in much the same way as a folding flash drive—another nod to consumer-friendliness and familiarity.

Types offered
Form factors
Back-of-box support
It was probably inevitable that Google would eventually get into the authenticator business, and when they did, inevitable that many wait-and-seers would decide that it was finally time to adopt multi-factor authentication. Google offers two authenticators:
Wireless PKI Authenticator (NFC)
Google Titan USB Security Key
Wireless PKI Authenticator (NFC+BLE)
Google Titan Bluetooth Security Key
Like Thetis, Google is aiming for simplicity—to cut through the jargon and layers of edge-case enterprise support to deliver simple MFA for today's systems. Google generally sells the devices in pairs—each pair containing a wireless token fob and a matching USB fob as a backup.
Factoid: Ironically it was Google that first justified the concerns of wireless authenticator critics, when a recall was issued for Titan Bluetooth models due to a vulnerability in the onboard Bluetooth stack. Google is now replacing early Titan Bluetooth units at no cost.
There are a few things to take away from this list, when all of the product families are considered together.

Hardware authenticators do add an extra layer of security—but they also add an extra layer of friction. © Tommaso79 / Dreamstime
Visual OTP is no longer cutting-edge. PKI authenticators are the future. With the entire world gradually moving to the cloud and cloud standards, FIDO and now FIDO2 are really the most important forward-looking areas of authentication infrastructure.
Wireless tokens are not an anomaly. The increasing shift toward a mobile-first world means needing authenticators that work with mobile devices and that are practical in the contexts where mobile devices are used. But, as Google Titan shows, there will be hiccups.
A credential is not a user. All of these devices are vulnerable in one way or another to theft—either of an OTP code or of an entire fob. Some makers are starting to add fingerprint scanners to fobs, but that ultimately doesn't solve the underlying problem.
Hardware authenticators add friction. In the end, even the slickest token device must be purchased, distributed, inserted, paired, or read, and even the slickest token adds an additional step to every single login interaction. In the case of tokens, more secure simply equals more friction.
All of this tends to point to our position at Plurilock—there's room in most enterprise environments for a variety of solutions to a variety of problems.
Those needing to add either login or continuous multi-factor authentication without additional costs or friction, however, should look beyond hardware tokens and toward solutions like Plurilock's ADAPT and DEFEND products. ■
Copyright © 2024 Plurilock Security Inc.